How Secure is Your Password?

This is an old article I wrote several years ago for another Web site which is no longer operational. Because several of the concepts in this article are still useful and applicable, I am publishing it here with the permission from the copyright owner. [Zubair Alexander]
In this article we will first look at how Windows stores passwords. Then we will discuss why pass phrases are a better option than passwords when it comes to securing your computer. Finally, we will look at several examples to determine the strength of our passwords.
How Windows Stores Passwords?
Instead of storing user passwords in clear text that can be easily detected, Windows NT/2000/XP/2003 stores passwords using two different representations (called “hashes”) for backward compatibility: LAN Manager hash and NTLM hash. This is true for passwords that are shorter than 15 characters. Windows stores the password in either local SAM database, or the Active Directory database, depending on the type of operating system and computer. To better understand how Windows stores these two different hashes, let’s look at some of their features.
LAN Manager Hash (less secure)
A LAN Manager hash is relatively easier to crack with brute force attack and should be avoided in government agencies & other secure environments. LAN Manager hash has the following features.
• Converts all lowercase characters in the password to uppercase
• Pads it with NULL characters until it’s exactly 14 characters
• Splits the password into two 7 character chunks
• Uses each chunk separately as a DES key to encrypt a specific string
• Concatenates the two cipher texts into a 128-bit string and stores the result
NTLM Hash (more secure)
An NTLM hash is relatively harder to crack and is recommended for Windows computers. NTLM hash has the following features.
• Sometimes referred to as “Unicode hash” because it supports full Unicode character set
• Hash is calculated by taking the plain text password and generating an MD4 hash which in turn is then stored in Active Directory or SAM database
Disabling LAN Manager Hash – Solution 1
In order to secure your passwords, you should consider disabling the less-secure LAN Manager hash whenever possible. For example, if you don’t have Windows 95/98 or Macintosh clients in your environment, you should disable LAN Manager hash using one of these three techniques described in the Knowledge Base article Q299656. Make sure you do not disable LAN Manager hash in an environment that contains earlier versions of Windows (i.e. pre-Windows 2000) or Macintosh computers. Otherwise, you will experience all kinds of problems as detailed in Q299656.
Disabling LAN Manager Hash – Solution 2
Another method is to use Group Policy to disable storage of LAN Manager hash. This can be achieved either through a domain policy, or via a Local Security Policy. For a domain policy follow the procedure described below.
Open Group Policy and go to Computer Configuration, Windows Settings, Security Settings, Local Policies, Security Options. In the right-hand pane double-click Network Security: Do not store LAN Manager hash value on next password change, select Enabled button and then click OK.
For Windows XP you can use the Local Security Policy to disable LAN Manager hash. Open Local Security Policy console, go to Local Policies, Security Options and in the right-hand pane double-click Network security: Do not store LAN Manager hash value on next password change. Click on the Enabled button and then click OK (see Figure 1 below). Make sure you change the password after you make this change.
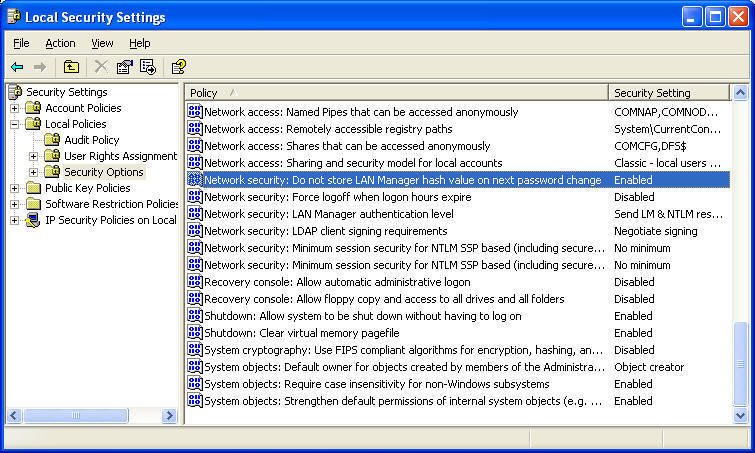
Figure 1 Disabling LAN Manager Hash Using Local Security Policy
Disabling LAN Manager Hash – Solution 3
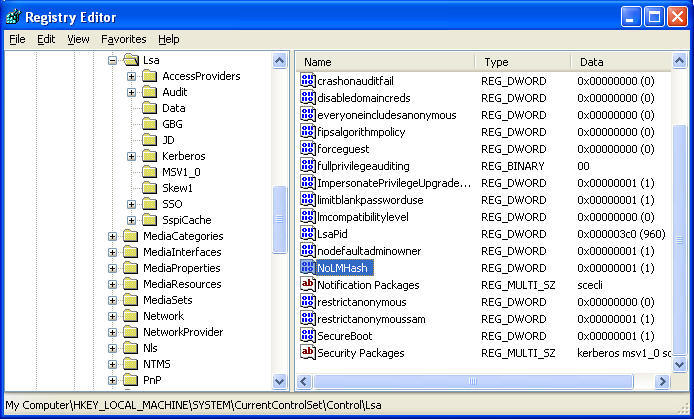
The third method is to modify the registry. For Windows 2000 SP2 and later, Windows XP, and Windows Server 2003, start the registry editor (regedit.exe) and go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa. From the Edit menu select New, DWORD Value and type NoLMHash then press Enter. Double-click the new entry, enter decimal value of 1 for the Value data, and click OK. Restart the computer for the changes to take effect and then change your password.
Figure 2 Disabling LAN Manager Hash Using Registry Editor
Pass Phrases vs. Passwords
In Windows networking environment we have been using passwords as an authentication method for a long time. IT departments have taught end-users how to use complex passwords so the bad guys can’t easily break into their systems. In Windows NT, the maximum password can only be 14 characters. In Windows 2000 Professional and Windows XP, users can use passwords that are up to 127 characters long. However, since every one in the industry always uses the term “password”, it’s natural for users to come up with one word without spaces that they use for a password.
I believe it’s about time that we start teaching everyone to use pass phrases, instead of passwords. Obviously, there are some of you out there who may be already doing that, and that’s great. For those of you who are still using passwords, you might want to consider using pass phrases. It’s hard for people to come up with long words, mixed with uppercase and lowercase characters, numbers, and special characters. It’s much easier to remember pass phrases. In addition, pass phrases with spaces can make a password longer, and therefore, more secure. For security purposes encourage users to use pass phrases longer than 14 characters. Longer pass phrases are not only harder to guess, they are also harder to crack with a password cracking program.
ALT-Key Combinations
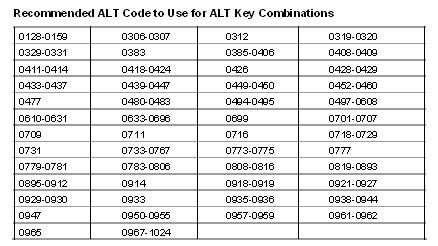
To make a pass phrase even harder to break, you can use Unicode characters in ALT-key combinations. For example, to enter a Unicode character €, you will hold down the ALT key and type 0128 on the numeric keypad. You must use the numeric keypad, the numbers above the keyboard will not work. There are some ALT-key combinations that are not recommended, such as ALT-0169 which is the copyright symbol ©, or ALT-0174 which is the registered trademark symbol ®, because these are automatically converted to uppercase C or R. Figure 3 lists the recommended ALT-key combinations that you should use.
Figure 3 ALT Key Combinations
Examples of pass phrases:
Let’s look at some examples of pass phrases. These examples will give you an idea of the types of pass phrases that might be easier to remember.
Good pass phrase:
I wish it would only rain 4 times each year
Better pass phrase:
I wish it would only r@in 4 times each Year
Even better pass phrase:
I wish it would only r@in 4 times €ach Year!
The last example has uppercase and lowercase characters, a number, special characters “@” and “!”, and an ALT-key combination “€”, which makes it a very good choice for a pass phrase. Not to mention the fact that it has a total of 44 characters, including spaces, which will make it very hard to crack. Obviously, it is also relatively harder to remember or type. Do you really need a pass phrase that’s 44 characters long? This next section on password complexity will help you decide what the best length may be for your environment.
Password Complexity Examples
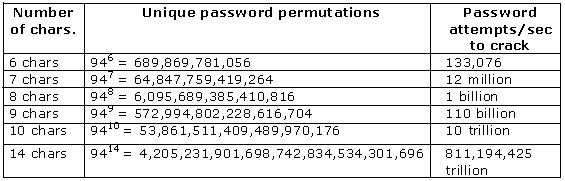
It’s interesting to note how adding only one or two characters to a password can make it exponentially secure. The following examples show how many attempts per second it will take to crack a password. The examples assume that your password expires in 60 days. You can easily calculate these numbers for your environment if the duration of your password expiration is different.
Password is 6 characters long, expires in 60 days
94 possible characters in the password
26 uppercase + 26 lowercase + 32 special + 10 numbers = 94
946 = 689,869,781,056 unique password permutations
Need 133,076 password attempts/sec to attempt all combinations
(946/60 days (5184000 seconds) = 133,076)
Password is 7 characters long, expires in 60 days
94 possible characters in the password
26 uppercase + 26 lowercase + 32 special + 10 numbers = 94
947 = 64,847,759,419,264 unique password permutations
Need 12,509,212 password attempts/sec to attempt all combinations
(947/60 days (5184000 seconds) = 12,509,212)
Assuming that the password expires in 60 days, if password complexity is enforced, the longer the password the harder it will be to crack, as shown below in Figure 4.
Figure 4 Password Permutations
Considering an average password cracking program takes about a million attempts per second to crack your password, you can imagine how long it will take to break even the first pass phrase in the above example that contains 43 characters (I wish it would only rain 4 times each year). The third pass phrase with 44 characters (I wish it would only r @ in 4 times € ach Y ear!) will be extremely hard to crack because it includes a Unicode character so the possible characters will be far more than 94.
Forcing the Use of Longer Passwords
On a Windows Server 2003 you can force users to use passwords longer than 14 characters by using ADSI Edit, as described below.
1. Start ADSI Edit.
2. Go to the domain object, e.g. DC=TechGalaxy,DC=net.
3. Right-click and select Properties.
4. Look for an attribute called MinPwdLength.
5. Edit the value and enter a new minimum length for the password. The default value is 7.
In Windows 2000 you can edit the .adm file to force users to use a password that’s more than 14 characters. In Windows Server 2003 this technique doesn’t work. In fact, if you try this in Windows Server 2003 and set the password length to more than 14 characters, you will get errors and the password length will be set to 7. Luckily, you can use ADSI Edit to work around this problem.
Conclusion
As you can see, using pass phrases is a much better idea than using shorter passwords. You should disable LAN Manager hash, if possible, and encourage (even force) users to use pass phrases that are longer than 14 characters. In a mixed environment where you have clients running earlier versions of Windows, this can break a lot of things. If your clients are running Windows 2000 or Windows XP you should definitely enhance your security by taking advantage of the techniques mentioned in this article.
Even if you are running Windows NT or Windows 9x computers on your network you can still improve your security by using NTLMv2 authentication. Your passwords will still be limited to 14 characters but NTLMv2 takes advantage of all 14 characters in your password, rather than the way LAN Manager authentication handles the passwords by breaking it down into two seven characters chunks, which are much easier to attack. Check out the article “How to Disable LM Authentication on Windows NT” (Q147706) for more details on this topic.
Additional Reading
- The Advantages of Using a Password Manager
- Selecting a Password Manager
- How Secure are Online Password Managers?
- Microsoft Authenticator to Allow Phone Sign In Without a Password
- Biometric Options from Microsoft and Apple
- How Secure is Biometric Authentication on Mobile Devices?
- How Secure is Your Password?
- Check Your Password Strength
Copyright © 2003- 2005 McCann Enterprises LLC.