How Secure is Biometric Authentication on Mobile Devices?

Before you read this article, I encourage you to read the precursor to this article: Biometric Authentication Options from Microsoft and Apple.
Mobile devices such as laptops, tablets, and smartphones offer the traditional password option to log into the device, but they also offer biometric authentication, such as fingerprint, iris, and facial recognition. These biometric authentication methods sure sound pretty high-tech, but are they secure and reliable? In this article, I will share my thoughts on this subject. Although biometric authentication is also available on desktop computers, it’s much more pervasive on mobile devices and therefore that’s where the focus of my article going to be.
Windows Hello
In Windows 10, Windows Hello offers the ability to use fingerprint, iris, and facial recognition to login to desktop computers, laptops, tablets, and Windows smartphones. If for some reason you can’t access the biometric sensor, it’s not functioning, or broken, a PIN is used as a backup.
I have covered Windows Hello authentication in much more detail in my article Biometric Authentication Options from Microsoft and Apple.
Windows Hello PIN
Windows Hello also allows you to log into your device with a PIN. What’s interesting about Windows Hello PIN is that it stays on the local device, unlike a password which can be intercepted during transmission. Even if your PIN is compromised, it will be useless without the actual physical device where it was created. In addition, Windows Hello PIN is backed up by the Trusted Platform Module (TPM) chip, which protects it from tampering and PIN brute-force attacks. Furthermore, the Windows Hello for Business PIN can be configured just like a password, with uppercase and lowercase characters, numbers, and even special characters.
I have covered Windows Hello PIN authentication in much more detail in my article Biometric Authentication Options from Microsoft and Apple.
Apple Touch ID and Face ID
On Apple computers, depending on the model, you can use either Touch ID or Face ID. These methods allow you to use your fingerprint (Touch ID) or facial recognition (Face ID), rather than the password, for many common operations such as making purchases from the iTunes Store, App Store, and iBooks Store. Apple replaced Touch ID with Face ID in iPhone X. Face ID uses facial recognition by mapping the geometry of your face and taking an infrared image of your face. User can simply look into the camera and unlock their mobile device.
I have covered Apple’s Touch ID and Face ID in much more detail in my article Biometric Authentication Options from Microsoft and Apple.
Biometric Authentication Reliability
In the past, biometric authentication methods, especially fingerprint, weren’t very reliable. There were a lot of issues with the hardware that was used and therefore people had to cross their fingers and hope it will work each time. Vendors were trying to compete and would offer cheap, unreliable hardware. Today the equipment used on the mobile devices is much better, but we still have a long way to go. Obviously, some devices are better than others. Products from reputable vendors are generally more reliable. Unfortunately, the vendors don’t publish the false positive rate so we don’t have any metrics to offer any judgement. Therefore, a user’s personal experience is what will determine the reliability. Overall, the biometric authentication is fairly reliable, but there is definitely room for improvement.
Biometric Authentication Security
As far as the security is concerned, I am not a big fan of any of the biometric authentication methods used on today’s mobile devices, regardless of the manufacturer. Not because they are all useless, primarily because these methods, such as fingerprint readers, iris scanners, and facial recognition have been hacked many times on all kinds of mobile devices offered by major manufacturers.
NOTE: Windows Hello PIN is perhaps one of the most appealing authentication method available on Microsoft Windows devices. It’s implemented in a secure manner, backed by the hardware (TPM chip), you can make the PIN complex just as a password, the PIN you enter won’t travel over the network, and even if your laptop is stolen the TPM anti-hammering protection can lock your laptop to offer better protection.
 The biometric technology used in most mobile devices today isn’t high-tech enough to provide the level of security that’s available on high-end systems. This may change in the future, but in recent years biometric authentication on mobile devices is not what it’s hyped to be. Besides the inability to provide proper protection from hacking, unlike passwords, these methods don’t work all the time. If you do an Internet search you will find many documented cases of these biometric offerings getting hacked either by security researchers to prove their point or by the hackers. Let’s examine a few of them.
The biometric technology used in most mobile devices today isn’t high-tech enough to provide the level of security that’s available on high-end systems. This may change in the future, but in recent years biometric authentication on mobile devices is not what it’s hyped to be. Besides the inability to provide proper protection from hacking, unlike passwords, these methods don’t work all the time. If you do an Internet search you will find many documented cases of these biometric offerings getting hacked either by security researchers to prove their point or by the hackers. Let’s examine a few of them.
Touch ID Hacked
In 2016, Russell Brandom wrote an article Your phone’s biggest vulnerability is your fingerprint. In his article he talked about the ease of hacking iPhone 6 and Galaxy S6 Edge.
“In five minutes, a single person faked a fingerprint and broke into my phone. It was simple, a trick the biometrics firm Vkansee has been playing at trade shows for months now. All it took was some dental mold to take a cast, some play-dough to fill it, and then a little trial and error to line up the play-dough on the fingerprint reader. We did it twice with the same print: once on an iPhone 6 and once on a Galaxy S6 Edge. As hacks go, it ranks just a little harder than steaming open a letter.”
I encourage you to read Russell’s article because he points out some very interesting cases, including one where a security researcher called Starbug created a working model of the German defense minister’s fingerprint using a high-resolution picture of his hand. You may also be interested in this article Why I Hacked Touch ID a(again) and still think it’s awesome.
5.6 Million Fingerprints Stolen
Because the FBI has over hundred million fingerprints in its IAFIS database and the government also has other fingerprint databases, these fingerprints can always potentially be used on a fingerprint reader. Remember the Office of Personnel Management (OPM) breach where 5.6 million fingerprints of federal employees were stolen? The OPM correctly said at that time that although the chances of an adversary misusing the fingerprint data are slim, “this probability could change over time as technology evolves”. By the way, the OPM was hacked twice in one year, presumably by the hackers with links to the Chinese government.
If you think about it, stolen fingerprints should be much more of a concern than stolen passwords because unlike passwords, the fingerprints cannot be changed. The U.S. intelligence community was most concerned about the theft of SF-86 forms during the breach. The SF-86 forms are filled out to obtain security clearances by federal government workers, military personnel, defense contractors, etc. If you are not familiar with this form, it’s a 127-page form. It’s more like a book compared to a typical form, and has all kinds of confidential information about a person.
Apple Face ID Hacked
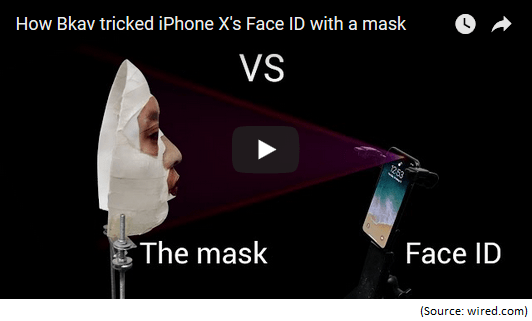
Apple replaced the Touch ID, with the more advanced Face ID in iPhone X, but unfortunately it too has been hacked. It was hacked by a Vietnamese security firm Bkav using a composite $150 3-D-printed mask, as reported by wired.com in the article Hackers Say They’ve Broken Face ID a Week After iPhone X Release. Watch the following Bkav 94-second video demo below.
While some experts questioned the legitimacy of Bkav’s discovery, they also acknowledge that this is the same company that demonstrated how to hack facial recognition on Asus, Lenovo, and Toshiba’s laptops and even presented their findings at 2009 Black Hat security conference. Bkav released another video a couple of weeks later on November 27, 2017 which demonstrated the Face ID spoof more convincingly.
Windows Hello in Windows 10 Hacked
When it comes to hacking biometric authentication, Apple isn’t alone. A couple of weeks ago security researchers from German firm SySS were able to show that if you have a printed photo of a user, you could use their photo login to a Windows 10 system. According to seclists.org:
“SySS GmbH could successfully bypass the configured Windows Hello user authentication with face recognition on two Windows 10 systems using a modified printed photo (paper printout) of an authorized user. For example, the spoofing attack was performed against a laptop device (Dell Latitude E7470) running Windows 10 Pro (Version 1703) with a Windows Hello compatible webcam [3] and against a Microsoft Surface Pro 4 device [4] running Windows 10 Pro (Version 1607) with the built-in camera.”
The researchers posted the following two proof-of-concept videos on the YouTube.
Windows 10 version 1607 was shown to be vulnerable, but the newer versions have been patched by Microsoft and are considered safe.
Androids Hacked
So far I have mentioned Apple and Microsoft devices. However, biometric authentication on Android devices have also been hacked over the years so they too have their own issues, as reported by New York Times in its article That Fingerprint Sensor on Your Phone Is Not as Safe as You Think. Toms’ Guide discusses the security issues on Samsung and Apple mobile devices in its article High Resolution Photos Fool Fingerprints, Iris Readers.
Why Biometric Authentication is Not as Secure as It’s Advertised
Microsoft Windows Hello and Apple Face ID offer significantly enhanced facial recognition options for authenticating to mobile devices and are generally considered secure. Windows Hello seem to have a much better track than Apple and Android devices. You could argue that compared to iOS and Android devices, not too many people use Windows 10 mobile devices and it hasn’t been around long enough for hackers to focus on them, and you may have a point. However, as a security professional I don’t feel comfortable using the biometric authentication methods on mobile devices for several reasons. The primary reason is that they have been hacked too many times. In addition, I also don’t like the risk to my privacy that mobile technology poses. When you sign into any cloud-based account (Google, Microsoft, Apple, etc.) your privacy is pretty much out the door because the purpose of a cloud-based account is to share your information with as many services, devices, and people as possible. For example, on an Android phone you are asked at the initial setup to use a Google account to interact with all the apps. A vast majority of people do not secure their Google account and are therefore vulnerable to hacking from the get go because they use most, if not all, of the default settings. They also don’t understand the nature of various Google services (Gmail, Google+, Google Drive, etc.) and how they interact. This makes them vulnerable.
You don’t really have to use a Google account on an Android phone, as I pointed out in my article Enhancing Privacy and Security Settings on Androids, but without using a Google account you will lose so much functionality that you probably won’t like using your Android at all. So what should you do? I suggest you use a Google account on an Android as long as you secure it. Some tips on securing your Android are available in my aforementioned article.
Final Thoughts
Just because I am a security professional and don’t like to use biometrics options available today on mobile devices, doesn’t necessarily mean that you shouldn’t either. My recommendation doesn’t apply to every single person. As a consultant I assess each individual case and then offer my advice accordingly. For example, if you tell me that for some reason (probably convenience) you are unlikely to use a passcode that’s more than 4 digits and I know that you have biometric options available to you on your mobile device, my recommendation would be to use one of the biometric option. Obviously, convenience is more important to you than security and you will be much safer by using biometrics than an easily hackable 4-digit passcode.
For those of you who are willing to give up convenience and have serious concerns about security, I suggest using a strong password, PIN, or a pattern for authentication and then multifactor authentication for your important apps, such as password managers, Web browsers, etc. As a best practice, always keep your devices updated with the latest updates. On Windows 10, consider taking advantage of the Windows Hello PIN. Hopefully, in coming years better and more secure authentication options will be available to us on mobile devices, such as multifactor authentication which may include a combination of several biometrics.
I mentioned earlier that unlike passwords, the fingerprints cannot be changed. JV Chamary pointed something out in his article on Forbes.com that I thought was interesting. He said that “One advantage of a passcode is that you might not be compelled to reveal it to police or government agents (customs, border control or FBI) if you invoke the Fifth Amendment, which protects American citizens from self-incrimination, whereas you could be forced to unlock your phone (or end-up in jail), which suggests that your face is vulnerable too.”
Let’s hope 2018 brings better security options for all mobile devices and wireless communications because people will continue to use mobile devices and wireless networks because of their convenience. The industry must find better solutions or continue to risk security and privacy of the individuals as well as businesses, military, and the government.
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.