Best Practices for Configuring Multi-factor Authentication in Office 365

Multi-Factor Authentication (MFA) is a security feature in Microsoft Office 365 which allows users to use a second authentication factor, along with their password. At the time of writing, multi-factor in Office 365 really means dual-factor authentication, but Microsoft may allow additional options in the future and that’s why the term multi-factor is used. By requiring an additional method, an attacker will have to not only enter the user’s password at the login prompt to sign in, but also acknowledge a text message, phone call, or app notification on the smartphone. Without this additional “factor”, the attacker cannot login successfully. This security feature is built into Office 365, but you can also pay for Azure MFA method to extend this functionality.
In this article, I will share some of the best practices for configuring MFA in Office 365. I will also share some best practices for configuring the Global Admin account.
Setting Up Multi-Factor Authentication
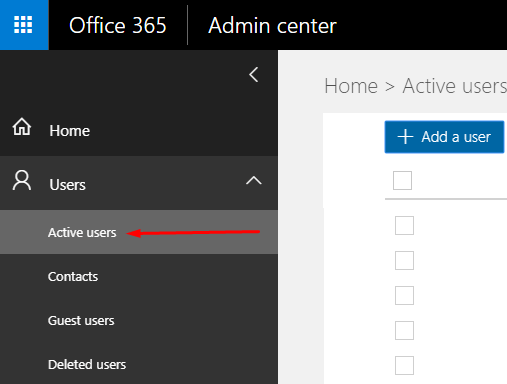
To setup an MFA, go to the Office 365 Admin center -> Active users.
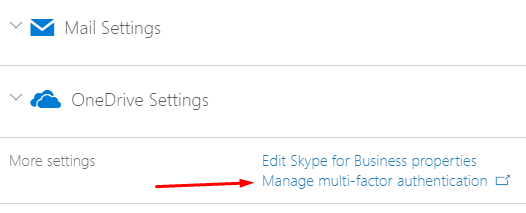
Select the user for which you want to enable MFA and under More settings click Manage multi-factor authentication.
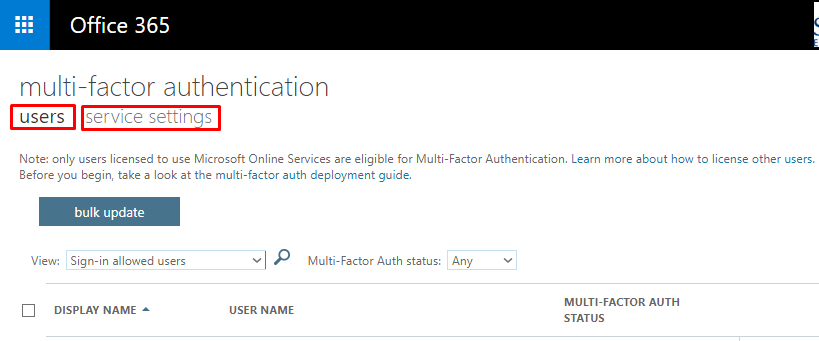
When you get to the multi-factor authentication screen, you will notice two links: users and service settings. On the Users tab you can select a user and then enable or disable MFA. I know, I called it a tab because it acts like a tab and it should have been a tab.
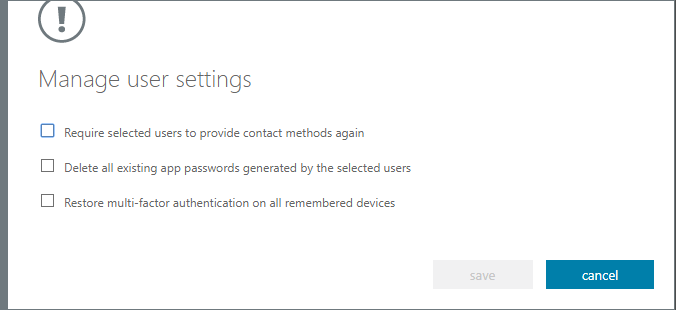
You can also manage the user settings, which gives you the options to take the following actions.
- Require selected users to provide contact methods again
- Delete all existing app passwords generated by the selected users
- Restore multi-factor authentication on all remembered devices
These options are pretty self-explanatory. You can select multiple users and apply these settings to all of them at once.
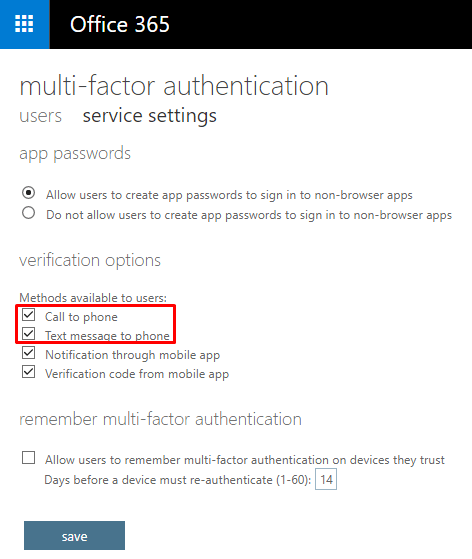
The second link on the multi-factor authentication screen is very important. It’s really easy to ignore this second link because this page design needs improvement. The two links should have been tabs and they should stand out. As you can see in the following screenshot, you can configure the option to allow users to create app passwords. This is very helpful and I recommend you always check the box to Allow users to create app passwords to sign in to non-browser apps. In addition, you can select the verification options for the users and decide how long you want the devices to remember the MFA before they are required to re-authenticate. The range is between 1-30 days and the default is 14 days.
Notice I have a red box around the first two options: Call to phone and Text message to phone. I like to check both of these boxes. Whether you want to give the users the option to get notification and verification code through mobile app or not that’s up to you, but if you don’t check the first two boxes you can potentially run into some problems. Check out the warning and then I will explain the reason for my warning. Notification through mobile app is my favorite option because it eliminates the need to enter any codes at all.
| WARNING! If you have MFA configured for your Global Admin account and you configured the verification options to include only the notification and verification with a mobile app, such as Microsoft Authenticator, you may lock yourself out if your smartphone app cannot be used because it’s not working; or your phone is lost, stolen, or damaged. |
What to Do if You Lock Yourself Out of Your Portal
There are several scenarios in which you can lock yourself out of your Office 365 portal, even if you are the Global Admin. If you forget your password, it can be reset easily. However, if you have MFA configured for your account without the call to phone or text message to phone options, you won’t be able to get in if your smartphone where the Authenticator app was installed is not available or not working. If you have another Global Admin account which can be used to login then you’re in good shape because you can login with that account and remove the requirement for MFA for the first Global Admin account and then add the MFA back after your phone has been replaced or fixed. When you setup the Microsoft Authenticator app on a mobile device, you use a QR code. If you install Microsoft Authenticator on a different smartphone, it will require a new QR code. The best thing is to make sure that you check the first two verification options in the above screenshot, so once you replace your damaged smartphone with a new one, you simply use the call to phone or text message to phone option as the second authentication factor to login. Because it’s unlikely that you will change your phone number when you purchase a replacement phone, you will not have to worry about getting locked out of your Office 365 portal.
Let’s assume you are a Global Administrator of a small company. You have configured your account AdminKatherine to sign in with MFA. You also create a backup Global Admin account called BackupAdminKatherine and configure it for MFA. One day you lose your phone and can’t get into your account because you don’t have access to the Authenticator app and your account is configured for MFA. If you call Microsoft Office 365 Tech Support you will be talking to their Tier 1 support. When you tell them your situation, ask them to reset the MFA on your account. They will have to escalate the case to Tier 2 support who have the ability to reset your MFA, provided they are able to confirm your identity. Once they reset your MFA, you will try to sign in to your account. You will see the option to setup your MFA. You will use the QR that is generated to add your Office 365 account to your Microsoft Authenticator app. You will enter the email and your password. When promoted for a code, you will use the code that is displayed on your Authenticator app on your smartphone to successfully sign in. The code changes every 30 seconds and you need to enter it before it expires. If the code wasn’t accepted, just wait for a new code.
If you were in a situation where you need to reset a forgotten password, that won’t be a problem because you can do that yourself easily on the login screen without calling Microsoft. However, resetting the password won’t affect the MFA and to complete the sign in process you must provide the second authentication factor.
If one of the standard user is having issues with his/her MFA, all you have to do is remove, or modify the MFA option. Keep in mind that if you make changes to the MFA options on the service settings screen it will affect all the users, including the Global Admin.
Best Practices for MFA in Office 365
Here are some best practices that you should consider for multi-factor authentication in your Office 365 tenant.
- Use MFA for all users to enhance security.
- Use MFA for Global Admins and other accounts with administrative privileges, even if you are not using it for the standard users.
- Microsoft recommends that you don’t configure MFA for one Global Admin account so it can be used for emergency access.
NOTE: When you configure security policy restrictions in Azure AD, Intune, etc., make sure you exclude Global Admins or else you can lock yourself out, even if you don’t have MFA enabled for your account. - As a general rule, configure Call to phone and Text message to phone verification options, in addition to the mobile app options. However, these options may not be ideal in every case.
- Use Microsoft Authenticator app on your smartphone for Global Admin accounts, because it is more secure than other verification options.
- Configure the option to Allow users to create app passwords to sign in to non-browser apps.
Useful Links
Here are some links that you may find helpful.
- Best Practices for Configuring the Global Admin Account in Office 365
- Microsoft Authenticator to Allow Phone Sign In Without a Password
- Office 365 Admin Help Center
- Office 365 Security Blog
- Office 365 Trust Center
- Office 365 Help and Training
- Setup Multi-Factor Authentication for Office 365 Users
Update: 11/4/2019:
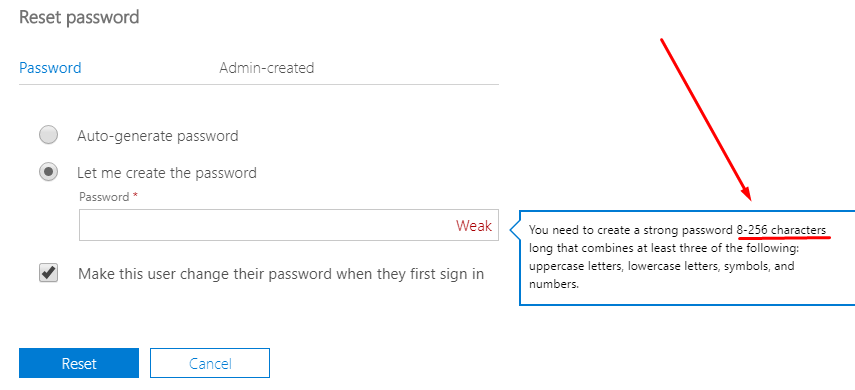
For years Microsoft only allowed a maximum of 16-character password in Office 365. Luckily, Microsoft is now allowing up to 256 characters in a password for Office 365 users. If you use a password manager, you can configure a 256-character complex password for the Office 365 Global Admin account that will be used for emergency access and always have a secure backdoor to your Office 365 tenant. As a precaution, make sure you exclude this, and all other Global Admin accounts, from security policies in Azure AD and Intune that block access to apps, features, and services.
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.