Biometric Authentication Options from Microsoft and Apple

Toshiba was the first mobile phone that offered a fingerprint authentication back in 2007. In 2012, Apple purchased a company that specialized in fingerprint reading, which resulted in Apple offering a fingerprint scanner in 2013 on its iPhone 5S. Microsoft offered its first biometric solution in 2015 in Windows 10 with the Windows Hello feature.
Today, most laptops, tablets, and smartphones offer the traditional password option to log into the device, but they also offer biometric authentication, such as fingerprint, iris, and facial recognition. Although biometric authentication is also available on desktop computers, it’s much more pervasive on mobile devices. The biometric solutions use passcode as a backup.
In this article, I will take a closer look at Microsoft and Apple’s biometric authentication methods and go into some details as to how they work.
Windows Hello
In Windows 10, Windows Hello offers the ability to use fingerprint, iris, and facial recognition to login to desktop computers, laptops, tablets, and Windows smartphones. If for some reason you can’t access the biometric sensor, it’s not functioning, or broken, a PIN is used as a backup. The PIN is created at the time you setup Windows Hello. The fingerprint reader lets you scan your fingerprints and compares it to the fingerprint images stored on your device. Similarly, the iris recognition takes a picture of your iris and compares it to the image stored on your device. In case of facial recognition, infrared (IR) light is bounced off your face, which the camera captures it. Your picture is then compared to the one that’s stored on your device. If it matches, you are authenticated and can access your device. These features are available on laptops, tablets, and smartphones and are often configured to be the default by some vendors. For example, you may find facial recognition turned on by default on certain Dell laptops.

Windows Hello PIN Authentication
Windows Hello authentication method is backed up by a PIN and because its support is built into Windows operating system, you can always add additional biometric devices as part of a Group Policy or Mobile Device Management (MDM) deployment. According to Microsoft, the biometric data is stored locally on the device and even if a hacker is able to get to the data, it can’t be easily converted to a format that a biometric sensor could understand. Microsoft provides a lot of technical details on Windows Hello biometrics in enterprise and Windows Hello facial recognition. Windows Hello also allows you to log into your device with a PIN. What’s interesting about Windows Hello PIN is that it stays on the local device, unlike a password which can be intercepted during transmission. Even if your PIN is compromised, it will be useless without the actual physical device where it was created. In addition, Windows Hello PIN is backed up by the Trusted Platform Module (TPM) chip. Because all Windows 10 Mobile Phones come with TPM, they can take advantage of the high level security mechanisms in place to guard the TPM against tampering and PIN brute-force attacks. Furthermore, the Windows Hello for Business PIN can be configured just like a password, with uppercase and lowercase characters, numbers, and even special characters. Because of all these advantages, a PIN is considered to be better than a password.
Apple Touch ID and Face ID
Touch ID: On Apple computers, you can use Touch ID on iPhone, iPad, and MacBook Pro. The Touch ID allows you to use your fingerprint, rather than the password, for many common operations such as making purchases from the iTunes Store, App Store, and iBooks Store. You can also use it to unlock your device, sign into apps, or use it with Apple Pay. In case you are wondering, the Touch ID doesn’t store your fingerprints on the device, it simply creates a mathematical representation of your fingerprint and compares it to the fingerprint data that’s already on your device. If it’s a match, it will unlock your device. The idea behind biometric authentication is to provide a more convenient and secure authentication than a traditional password because it’s difficult to enter a long, secure password on a mobile device. However, if Touch ID can’t read your fingerprint, after 5 unsuccessful attempts, it falls back to the password authentication. This means that a hacker who has physical access to the device, can easily bypass the biometric authentication and try to hack the password. As a best practice, you should not rely just on your fingerprints being unique, make sure your password is also strong.
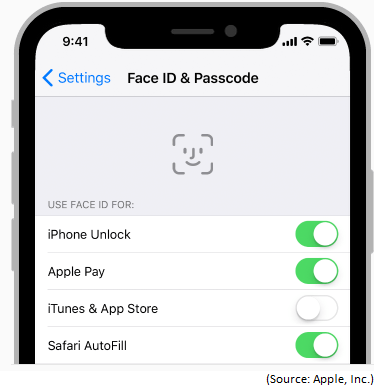
Face ID: Apple replaced Touch ID with Face ID in iPhone X. Any app that supports Face ID automatically uses it to let the user sign in. To map the geometry of your face, Face ID not only projects and analyzes over 30,000 dots on your face to crate a depth map, it also takes an IR image of your face. Similar to Touch ID, after 5 unsuccessful attempts you will be required to use your passcode. Again, this means that Face ID will allow a hacker with physical access to your phone to easily bypass the “secure” biometric method of authentication and fall back to the passcode option. Apple’s reasoning behind this logic is that Face ID is secure because people who don’t use passcode at all are encouraged to use Face ID and are therefore protected. It’s a rather strange logic because it tells me that Face ID, supposedly more secure than the Touch ID, was designed for people who absolutely don’t care about security and don’t even use a passcode to lock their mobile devices.
Because the children features are still developing, Apple suggests that if you have any concerns then for kids under 13, twins or siblings, use the passcode instead of Face ID. The passcode is always used as a backup in situations when the device has not been unlocked for over 48 hours, just been started, etc. According to Apple:
“Face ID automatically adapts to changes in your appearance, such as wearing cosmetic makeup or growing facial hair. If there is a more significant change in your appearance, like shaving a full beard, Face ID confirms your identity by using your passcode before it updates your face data. Face ID is designed to work with hats, scarves, glasses, contact lenses, and many sunglasses. Furthermore, it’s designed to work indoors, outdoors, and even in total darkness.”
Biometrics and Security
What about the security issues with the fingerprint, iris or facial recognition? Can someone steal your fingerprints or create a look-alike facial mask to login to your mobile device? Check out my article How Secure is Biometric Authentication on Mobile Devices? for answers to these questions.
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.


