Password Recommendations for Microsoft Accounts

Microsoft Accounts are used to sign into Microsoft Office 365, Outlook.com, OneDrive, Skype, Windows Phone, Xbox Live, and other Microsoft services
For the past couple of decades, Microsoft has recommended using longer, complex passwords and forcing users to reset their passwords frequently. In Windows NT, Microsoft allowed a maximum password length of 14 characters and no spaces. For the later operating systems, Microsoft increased this length to 127 characters and allowed passphrases (passwords with spaces). Today in Windows 10, Microsoft has decreased the password length to 63-character passphrases on the PC. For the cloud services, such as Office 365 and Outlook.com, the maximum password length has been further decreased to 16 characters and spaces are not permitted. Although Microsoft keeps decreasing the maximum password length for its software, the other major vendors have not followed this trend for their cloud services. For example, Google continues to allow up to 100 characters passphrases for Gmail.
| UPDATE: As of May 14, 2019, Microsoft supports 256-character passwords in Azure Active Directory (Azure AD). You can also use spaces in your password. See details in the Update section at the end of this article. |
For Microsoft Office 365 and other cloud-based services that use Microsoft Account, Microsoft’s recommendation is to set the Office 365 user passwords to never expire. As far as the recommended password length, Microsoft suggests users should stick to 8 characters, which is also the default minimum value for user passwords in Microsoft Office 365. On surface, this seems like a strange recommendation from Microsoft because it contradicts with what Microsoft has said in the past. However, that was then. This is now. If you take a closer look, the new recommendation from Microsoft makes sense as long as you understand why Microsoft is making these suggestions. Microsoft has documented these recommendations in a Microsoft Password Guidance paper written by several Microsoft identity protection experts and researchers. The password guidance primarily apply to Microsoft accounts, but can also be used in other places. First, let me define what a Microsoft Account is and then I will talk about the various password guidelines for administrators and users in Microsoft Office 365.
What is a Microsoft Account?
A Microsoft Account is an account used to sign in to Microsoft Office 365, Outlook.com, OneDrive, Skype, Windows Phone, Xbox Live, or other Microsoft services. For example, accounts created at live.com, outlook.com, hotmail.com, or msn.com are all called Microsoft Accounts. These are domains owned by Microsoft and provide various Microsoft cloud-based services.
Password Recommendations for Microsoft Office 365
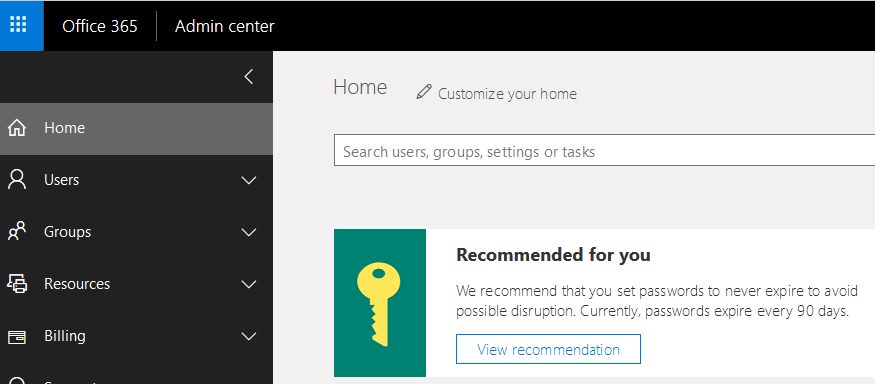
If you are a Microsoft Office 365 Global Administrator, you may have noticed the following recommendation on your dashboard under the heading Recommended for you:
“We recommend that you set passwords to never expire to avoid possible disruption. Currently, passwords expire every 90 days.”
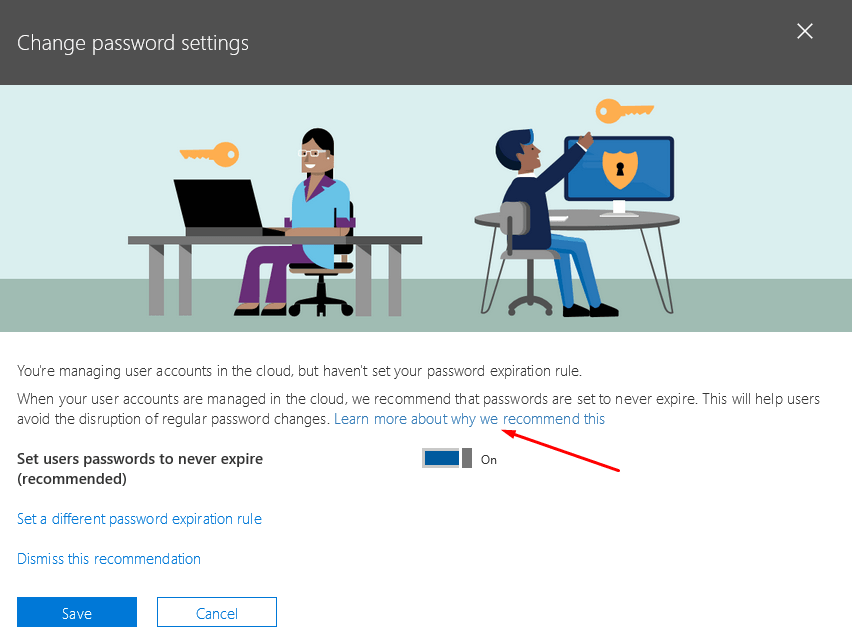
When you click on the link View recommendation, you will see the following screen, which gives you the option to set user passwords to never expire.
Clicking the link Learn more about why we recommend this will take you to the Microsoft Password Guidance PDF file. It’s a 19-page document full of useful information related to password guidance, which are essentially password best practices for both administrators and the end users. The paper includes not only Microsoft’s research efforts, but also the lessons Microsoft has learned from its experience as one of the largest identity providers in the world. I highly encourage everyone to read this paper.
Password Guidelines for the Administrators
Microsoft’s recommends the following password guidelines for IT Administrators. For detailed explanation of each of the following topics refer to the Microsoft Password Guidance document.
- Configuring an 8-character minimum password length is reasonable because longer passwords aren’t necessary better.
- Force multifactor authentication for all users.
- Enable risk-based multifactor authentication challenges.
- Set the passwords to never expire for all users. There is no good reason to make users change their passwords occasionally.
- Train users to use their work passwords only at work and not at home or elsewhere.
- Common passwords should be banned. These include 12345678, abcdefgh, password, etc.
- Don’t require character-composition.
Password Guidelines for the Users
Microsoft recommends the following guidelines for the users. For detailed explanation of each of the following topics refer to the Microsoft Password Guidance.
- Avoid using the Microsoft account password on other sites
The advantage of using unique passwords is that if your Outlook email is hacked, the hacker won’t be able to use the same password to access your other sites. - Keep your security information up to date
The security information (e.g., alternate email, phone number, etc.) is used by Microsoft and other vendors to send you security notification and is also used to reset the password. - Use Microsoft Authenticator app on your mobile device
The Microsoft Authenticator app will allow you to quickly verify your identity. It also works with the multi-factor authentication (MFA) for your Microsoft account. For more information on setting up Microsoft Authenticator app on your smartphone see Microsoft Authenticator to Allow Phone Sign In Without a Password. 
- Use MFA whenever it’s available
Multi-factor authentication can be used in many places today (e.g., Office 365, Outlook.com, password managers). If MFA is available, you should use it. When you use MFA, even if the attacker knows or guesses your password, without having access to the Microsoft Authenticator app on your mobile device, the attacker won’t be able to access your account. For more information on how to configure MFA for Office 365 see Best Practices for Configuring Multi-Factor Authentication in Office 365. - Avoid using personal information or common words in your passwords
You should not use personal information about you or your family in a password because hackers can either guess or look up information about you from public Web sites (e.g., Facebook, Twitter, Google, public records search, etc.). The common words, names, flowers, animals, etc. are too easy to crack with a dictionary or brute force attack. Here’s a list of 100 most common passwords. Let’s hope your password is not on this list. - Always keep your operating system, applications, and web browser up to date
Keeping your system and apps patched with security updates will provide better security and privacy. - Be suspicious of emails from strangers and unknown websites
To protect yourself from phishing and other malware attacks, don’t open emails from users that you don’t recognize and avoid opening unfamiliar attachments. Watch out for free downloads from unknown sources on the Internet. These are common means used by hackers to spread malware. - Make sure you have an anti-malware software installed on your computer
Anti-malware software should be kept up to date. It will protect you from viruses, spyware, keyloggers, and other harmful malware. There are many free anti-malware software available to you, including the builtin Windows Defender on Windows 10. - Use Microsoft Passport and Windows Hello features in Windows 10
Because Microsoft Passport replaces passwords with multi-factor authentication, it offers better protection and provides secure authentication to Active Directory (AD), Azure AD, and Microsoft Account. Windows Hello supports biometric authentication so instead of a password you can use fingerprint, iris scan, or facial recognition to log in to Windows 10. For more information on Windows Hello see Biometric Authentication Options from Microsoft and Apple.

Summary
Here’s a summary of recommended steps for using passwords with Office 365 and other services that use Microsoft Account.
- Install Microsoft Authenticator app on your mobile device. You can download it from Google Play for Android smartphones or from iTunes for iPhone/iPad.
- Use a complex password that’s between 8-16 characters AND use multi-factor authentication.
(See the update at the end of this article regarding password length.)
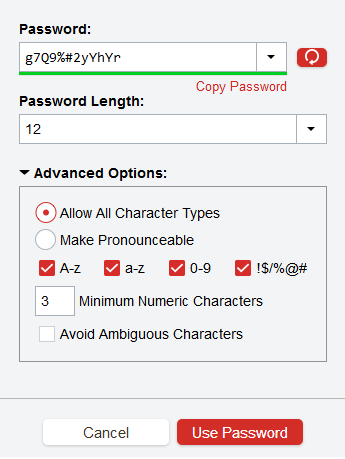
- Although Microsoft didn’t mention using a password manager in its paper, I highly recommend using a password manager so you can setup complex passwords without the need to memorize them. There are several Advantages of Using a Password Manager and most of the password managers also support using the same authenticator app and multi-factor authentication that you use with Office 365. In addition, most password managers also include a password generator (see image in step 2 above), which makes it easier to generate complex passwords and quickly paste them in the password manager. There are several articles related to password managers listed in the Additional Reading section below.
| Best Practice: From a security and privacy perspective, two of the most important things to consider are using a password manager and taking advantage of the multi-factor authentication whenever it’s available. |
If you are unable to access the Microsoft Password Guidance paper on Microsoft’s Web site, you can download it here. However, keep in mind that this is the original copy of the document that was published in June 2016 and may not be up to date.
UPDATE:
On May 14, 2019, Microsoft Azure Team announced that Microsoft now supports 256-character passwords in Azure Active Directory (Azure AD). Although it hasn’t been officially announced, and Microsoft documentation will take time to catch up, you can now use spaces in the password. This means that Microsoft Office 365 users can use password phrases (passwords with spaces) between 8-256 characters long.
My recommendation is to use a 256-character password at least for your administrative accounts (if not all accounts) by letting your password manager generate it. Make sure it includes:
- Uppercase letters
- Lowercase letters
- Numbers
- Special characters
Save your password in your password manager and always use multi-factor authentication for every single account in Azure AD, with one exception. Based on Microsoft’s recommendation, at least one of your emergency access accounts in Azure AD should be excluded from phone-based multi-factor authentication.
Additional Reading
You may find the following articles useful. They are all related to the topics discussed in this article.
- Microsoft Authenticator to Allow Phone Sign In Without a Password
- Best Practices for Configuring Multi-factor Authentication in Office 365
- Biometric Authentication Options from Microsoft and Apple
- How Secure is Biometric Authentication on Mobile Devices
- How to Sign-In to Windows 10 With a Non-Microsoft Account
- The Advantages of Using a Password Manager
- Selecting a Password Manager
- How to Setup LastPass for PIN Authentication on Your Smartphone
| Thanks for reading my article. If you are interested in IT consulting & training services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.