Why Can Apps Be So Dangerous?

All computer apps, whether they are designed for your desktop computer or mobile devices, have one thing in common. They ask for your permissions to get access to certain parts of your desktop computer or mobile device. A lot of users don’t realize exactly what this means. They do know that in order for the app to work, it needs certain privileges so they click Accept and start to use their cool apps. However, they don’t realize what exactly they did when they gave an app permission. How many people read and understand the permissions an app is requesting and realize the consequences of installing the app? Have you ever wondered, why would a Flashlight app need access to your camera to take photos and videos? Did you know that the permissions that are listed during installation, are not necessarily all the permissions that you are actually giving to an app? I am not saying that the apps always ask you for permissions they don’t need. I am simply raising awareness so you can better protect your privacy and be aware of what the mobile apps are doing. There are several reasons why the apps can be so dangerous and knowing what they can do is helpful.
In this article, I will dig deeper into the “who, what, where, and when” of the app permissions. I will primarily focus on the apps for mobile devices because that’s where the majority of apps are used and that’s one of the reasons why mobile devices are a mecca for cybercriminals. For the purpose of this article, the word “computer’ refers to both desktop computers and mobile devices (laptops, tablets, smartphones, etc.). In addition to the Windows apps (a.k.a. Store apps), on desktop computers you can also use desktop apps, but on the mobile devices you use mobile apps which behave differently than the desktop apps. Compared to a wired computer on a private network, it is way too easy to hack into a mobile device that’s completely dependent on the less secure wireless technology and……you got it……apps.
It is not easy to protect your privacy on a mobile device. One way to protect your privacy is to not use apps on the smartphone, but that would be like eating pizza without cheese. Who wants that? Your smartphone without apps will neither be smart nor a phone. The operating systems for mobile devices are designed to use apps because that’s how all the vendors make millions of dollars. Understanding the permissions apps require is key to understanding the security and privacy risks associated with your mobile device. So let’s dig deeper on what types of permissions apps usually request.
The Types of Permissions Requested By the Apps
Whether the app was developed by an independent developer or by a large corporation, it usually wants to take over your entire farm so you can do your tasks with few or no interruptions. Would we share our personal phone contacts and private images or videos with a complete stranger who has no photo on the Facebook? Hopefully not, but we have no trouble sharing them with an app that may be written by some Joe Shmoe in his basement in Timbuktu. When we use smartphone we automatically assume, everyone is using it so our privacy must be protected. The wireless technology has been pushed out to consumers probably twenty years too early, before it was secure and ready for the prime time.
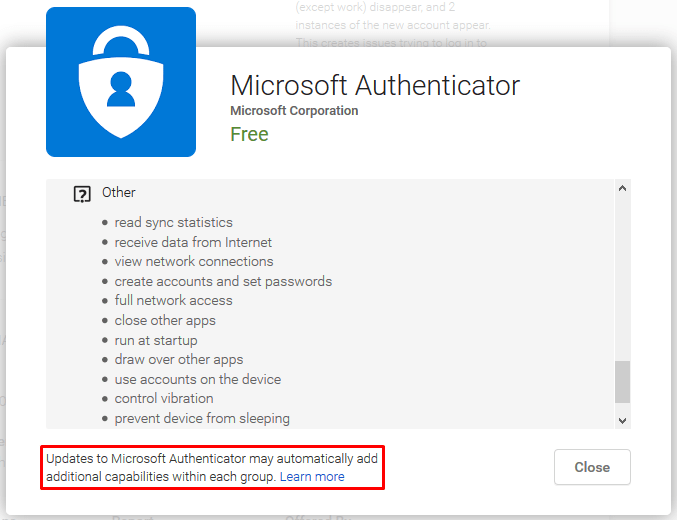
Here’s an example of an app developed by Microsoft called Microsoft Authenticator. It requires the following access.
NOTE: I am using Microsoft Authenticator app as an example in this article because I have already done some research on this app for my last article. Also, this app has a lot of permissions so it’s a good example for demonstration purposes. However, this could be any app from any company, big or small. Because this app was developed by Microsoft, I feel comfortable using it.
- Identity (access all the accounts on your phone, use accounts on the device, read or remove accounts, read your own contact card)
- Contacts (read your contacts)
- SMS (access to your text messages, including any photos or videos that people may text you)
- Photos/Media/Files (all images, audio recordings, video recordings, anything in the device’s external storage, access to the USB storage to modify or delete content)
- Camera (take pictures and videos)
- Device ID and Call information (this includes your phone number, device IDs, whether a call is active, and also the remote phone number that is connected by a call, such as the phone number of your friend, relative, neighbor, girlfriend/boyfriend, babysitter, dentist’s office, or anyone else that you are talking to)
- Other (by installing the app, you also give the following permissions to the app)
- Read sync statistics
- Receive data from Internet
- View network connections
- Create accounts and set passwords
- Full network access
- Close other apps
- Run at startup
- Draw over other apps
- Use accounts on the device
- Control vibration
- Prevent device from sleeping
- Toggle sync on and off
- Future Capabilities (updates to the app may automatically add additional capabilities within each of the above 7 categories without your knowledge)
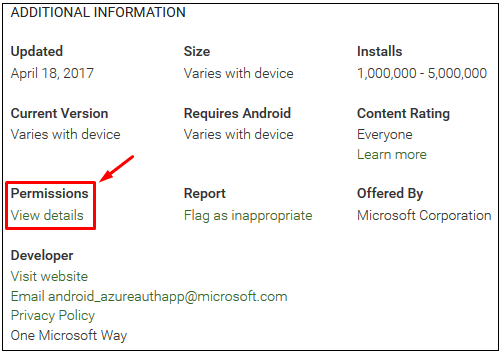
Initially, you will see the first 6 items on the above list. If you start digging, like I did, you will find more permissions that weren’t advertised when I installed the app. With app updates, the door is left wide open for the developers to add just about anything they want. When you update an app, it may make changes to the functionality and give itself additional permissions. Do you know what they are? No, you don’t because the updated doesn’t tell you that. You will have to manually look for those permissions. Even if you find them, would you know if they are different from before? Most likely, not. The above screenshot is from Microsoft Authenticator app on Google Play. The information is listed under View Details.
Microsoft Authenticator is an identity verifier app so it obviously needs a lot more access than some other apps on your phone. However, if you look at the apps on your mobile device, you will notice they too demand a lot of access. Who is asking for the access and do they really need all the access is a matter of concern because you don’t have the ability to accept some permissions (e.g. prevent device from sleeping) but not others (e.g. camera or your videos). It’s all or nothing.
NOTE: I didn’t use Microsoft Authenticator as an example to discourage you from using it. I believe it’s an excellent identity verification app. That’s why I use it and recommend it to others. For more information, please read my article Microsoft Authenticator to Allow Phone Sign In Without a Password.
Are There Any “Hidden” Permissions?
The list of permissions in the previous section is displayed when you download an app. If you think these are all the permissions that you are giving to the app, you are sadly mistaken. These are only the “most important” permissions. For a full list of permissions you have to do some research. I wouldn’t call them “hidden” permissions because they are listed somewhere, it’s just that you have to poke around until you find all the permissions. Luckily, I have done some research to make it easy for you to find the not-so-visible permissions. For example, if you download an app from Google Play, according to Google:
“You’ll see the most important permission groups on every download screen. If you want to see the full list of permissions an app can access on your device, follow the instructions under “See all permissions for a specific app” below.”
The See all permissions for a specific app section describes how to look at the additional permissions. Here’s how you can get to it.
For a Computer App:
- Go to play.google.com/store.
- Go to an app’s detail page.
- Under Additional information, look for Permissions and select View details.
For Android Apps You Haven’t Downloaded Yet
Use the Play Store app:
- Open the Play Store app.
- Go to an app’s detail page.
- Under Developer, tap Permission details.
For Android Apps You’ve Already Downloaded
Use the Settings app on your device:
- On your device, open your main Settings app.
- Depending on your device, tap Apps, Apps manager, or Application Manager.
(You will find Microsoft Authenticator listed as Authenticator in App manager) - Select an app.
- Scroll down to Permissions.
(You may have to click Show more at the bottom of the screen to see more permissions)
Different Permissions Everywhere
One of the frustrating part is that depending on where you find the permissions, you will see a different list. I don’t know if the inconsistency is on purpose, accidental, or simply incompetency. I guess I will have to call one of my developer friends and get the inside scoop about this inconsistency. In case of the Authenticator app, when I downloaded and installed the app, it displayed a set of permissions, when I went to the Google Play store on my computer the permissions list was slightly different for this app (it had a more comprehensive list) than the first list, and when I looked at them under the Developer section of the app on my phone the permissions were slightly different than the other two lists, and when I went to the App manger the list was different than the other three lists. What I get from this is that it’s almost impossible for you, the user, to know exactly what permissions or access you are giving to the app because they are inconsistent all across the board. It sure would be nice if we, the consumers, were able to look for permissions in one place and they were accurate and updated with each automatic update of the app.
Why Are Free Apps So Dangerous?
Now that we know about the types of permissions and their inconsistency, let’s talk about the dangers associated with the free apps. People like free “stuff” and apps are no different. The free apps are considered more dangerous than paid apps for several reasons. The developers of free apps make money by advertising or gathering your information. Therefore, they include ads in their apps. This could be extremely dangerous, even if the app was created by a well-known, reputable company. Why? Because these companies verify that the apps are safe in the sense that they don’t contain malware, but they don’t check the ads that are displayed inside an app for malware or security vulnerabilities. By clicking an ad, the user can be sent to a malicious site operated by a hacker or a cybercriminal, which could lead to installation of malicious software on the user’s mobile device.
If a hacker wants to infiltrate a network or a device, writing a free app will be one of the easiest thing to gather data from the users. Imagine all the permissions users are giving to the app. The app can have access to the employees contacts, images, videos, text messages, complete network access, all the incoming and outgoing calls, and even the camera. This gives the app pretty much complete access to your mobile device. The user installs the free app and the hacker can have full access to the mobile device. If the user works for a company, chances are the contact information of the fellow employees is in the contacts list. The fake antivirus programs are not the only trap cybercriminals use as a bait, they also like to use free mobile apps with ads to lure innocent people. It doesn’t take hundreds of employees to fall prey to the cybercriminal before an organization can be infiltrated, it only takes one.
Hopefully this will help you understand why free mobile apps are a privacy risk not only for the individuals, they are also very dangerous for organizations because most companies don’t make investment in securing mobile devices, until they have to pay a hefty price like a major security breach. Just look at the big organizations like Premera Blue Cross, Home Depot, Target, and thousands of other businesses and Web sites that have experienced major security breach. Although apps were not the reason for security breach in these cases, the important point to note here is that companies often fail to secure their network until they get hacked. In case of Premera, the federal auditors warned Premera three weeks before the hack that its network security was inadequate and yet Premera failed to protect 11 million patient records from being stolen, as reported by The Seattle Times in the story Feds warned Premera about security flaws before breach. While security is important to all businesses, those who allow employees to use mobile devices for business purposes need to take extra care because mobile devices and Internet-of-Things (IoTs) are a prime target of cybercriminals.
Keep in mind, some free apps are harmless while the other can run in the background and collect user’s personal data, credit card information, and other confidential data that can be used to steal identity. The moral of the story is this. Free apps can be dangerous, including those created by reputable companies, if they include ads. Obviously, all free apps are not dangerous. To avoid risking your security and privacy, only use free apps from reputable companies, like Microsoft, and make sure they do not contain any ads. If they do contain ads, do not click on them. As I pointed out earlier, the ads are usually included with free apps made by independent developers. They are not bad people, its just that they depend on ads to make some profit and there is no way for them to verify every single ad for malicious intent.
NOTE: Although Microsoft Authenticator app is a free app, it contains no ads and is safe to use. It offers a secure way of signing in to your phone without a password.
According to PrivacyRights.org, “Advertisers pay app developers to get access to you. The advertisers supply code to the app-makers to build into the app. The code not only makes an ad appear when you use the app, but also collects data from your phone and transmits it back to the advertiser. It’s also possible that the app itself collects data which is shared with ad networks. The ad networks may then show the user ads that contain content based on the data collected.
The data collected and/or shared can be used to build a detailed profile about you, re-packaged and sold to the highest bidder.
In December 2010, the Wall Street Journal investigated 101 apps to see what data the apps were sharing with advertisers. It found that 56 apps shared the phone’s unique ID number, 47 transmitted the phone’s location and 5 shared the user’s age and gender and other personal details (like phone number or contacts list).”
Apps Can Be Dangerous, But Can They Cause Death?
There have been several recorded incidents where an app has been blamed for death. There are different ways that an app can kill people. Here are some examples.
- Last year two Israeli soldiers got lost using the navigation app called Waze on their smartphone. They ended up in Palestinian territory in West Bank. A gun fight ensued that left a Palestinian man dead. New York Times reported this story on March 1, 2016.
- According to Mirror, the soldiers in Afghanistan used an iPhone app based on a computer game to kill Taliban fighters. In a 2012 article, Susie Boniface reported:
“BulletFlight helps sharpshooters work out how the wind and the rotation of the Earth will affect their bullet – and even predicts the wounds the enemy will suffer if it hits him. Snipers are using the ballistics program downloaded on to their iPhones to target the enemy over long distances. Allied forces already use adapted Xbox 360 video game controllers to pilot robotic vehicles.” - Apple’s iOS Maps app was so bad that the CEO Tim Cook publicly apologized for it and the Australian police issued a public warning telling them that the app is so bad it might kill you. Why? Because the app was telling people that Mildura was in the middle of a national park when it was actually 70km away. There was no water in the park and the temperatures were extremely high, posing serious life-threatening situations for the travelers. According to bgr.com,”Some of the motorists located by police have been stranded for up to 24 hours without food or water and have walked long distances through dangerous terrain to get phone reception.” The police in Victoria had to rescue six people over a two month period all because of Apple’s Maps app.
- According to NBC News, the same group of Russians who hacked into DNC and got someone to click on a spear-phishing email, came up with an ingenious plan to kill Ukranian soldiers. A Ukranian military officer developed a smartphone app that allowed the soldiers to shoot their weapons in seconds, rather than minutes, against the Russian-backed separatists. He distributed the app through his social media page. The app was also showed on the YouTube, which turned out to be a bad idea because the Russians hacked into the Android app shortly after the YouTube demonstration. The Russians used geo-location to track the Ukranian army and kill them. According to The Washington Post, “Ukrainian artillery forces lost more than 50 percent of their weapons in the two years of conflict and more than 80 percent of their D-30 howitzers, the highest percentage of loss of any artillery piece in their arsenal.” Unfortunately, they also lost a lot of lives as a result of these Russian hacks.
While apps can sometime be responsible for killing people, they can also save lives. Check out my article UW Develops an Android App that Detects Signs of Sleep Apnea.
Other Privacy Articles
Here are some of my other privacy-related articles that you may be interested in.
- Microsoft Authenticator to Allow Phone Sign In Without a Password
- Allowing Consumers to Protect Their Privacy and Opting Out of Receiving Junkmail
- Google in Trouble Over Privacy Issues (Again)
- Google Street View…or is it candid camera?
- How to Prevent Browsers from Sending Your Location Data to Web Sites
- How to Sign In to Windows With a Non-Microsoft Account
- Is Google the Dennis Rodman of Technology Industry?
- IT Leaders Trust Microsoft More Than Google…..Duh!
- Microsoft “Phoning Home” Once Again…..Then Backing Down Somewhat
- Microsoft and Google Plan to Get Rid of Cookies in the Browser
- Privacy International Ranks Google as “hostile to privacy”
- Survey Finds 60% Facebook Members May Quit Over Privacy Concerns
- When Microsoft Says No, It May Mean Yes
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2017 SeattlePro Enterprises, LLC. All rights reserved.