Difference Between Multi-Factor Authentication and Multi-Step Authentication

The terms multi-factor authentication and multi-step authentication are sometimes used interchangeably, but they are two different things and it’s important to understand the distinction between them. In this article I will use several examples to explain the difference between them. First, let’s talk about multi-factor authentication and then we will look at the multi-step authentication.
Multi-Factor Authentication
Multi-factor authentication (MFA) refers to using multiple forms of authentication, such as a password and retina scan. There are two distinct factors that are used for authentication. If the hacker steals your password, a totally different form of authentication (retina scan) is still required to gain access. If only two factors are used then we refer to it as two-factor authentication (2FA). However, technically multi-factor means two or more factors so people often use the terms multi-factor authentication and two-factor authentication interchangeably.
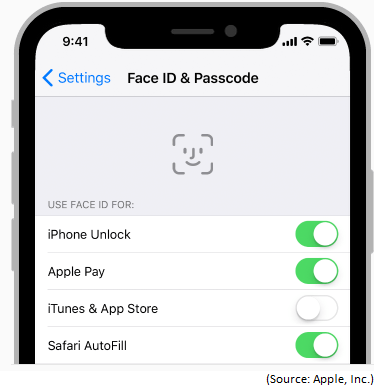
In case of Apple’s Face ID and Passcode, there are two types of factors involved. Something a user has (face) and something the user knows (passcode). Therefore, this form of authentication is technically a 2FA, but calling it MFA will also be appropriate.
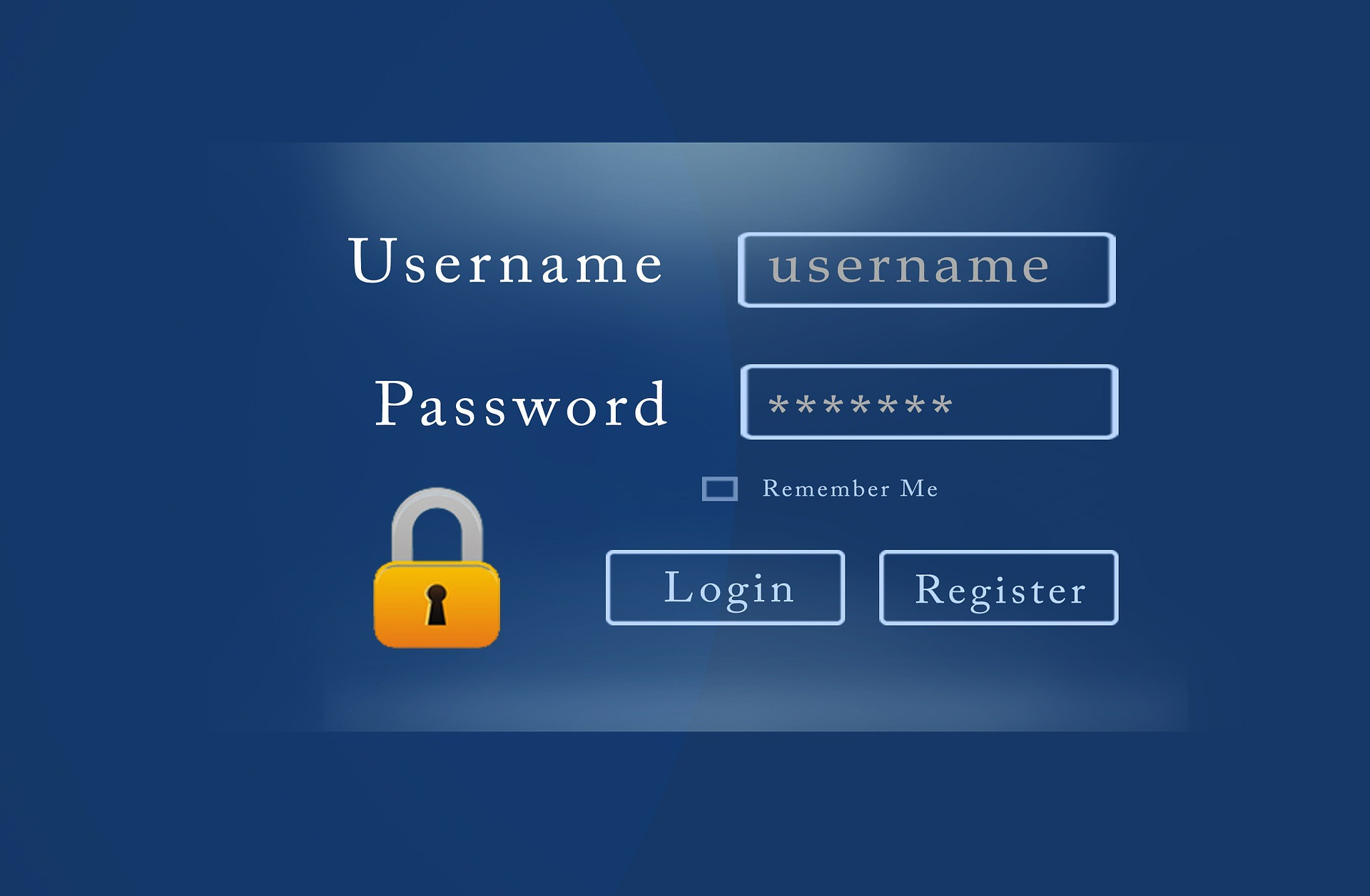
What about username and password? Is that an example of MFA? The commonly used username and password authentication method falls under the single-factor authentication (SFA) method because the username and password are both part of the same category. A user enters one type of information in the first box (username)and another type of information (password) in the second box. They are both pieces of information (knowledge) that the user has.
Multi-Step Authentication
In a multi-step authentication, there are multiple (two or more) steps involved. However, the steps use the same form of authentication. For example, using two steps in which you provide two different passwords to get authenticated to a device, or using two biometric forms of authentication, such as retina scan and fingerprint to get authenticated to a system. These two steps are using the same type of authentication so this is an example of multi-step authentication, which is not the same as multi-factor authentication. If only two steps are used then we refer to it as two-step authentication. However, technically multi-step means two or more steps so people often use the terms multi-step authentication and two-step authentication interchangeably.
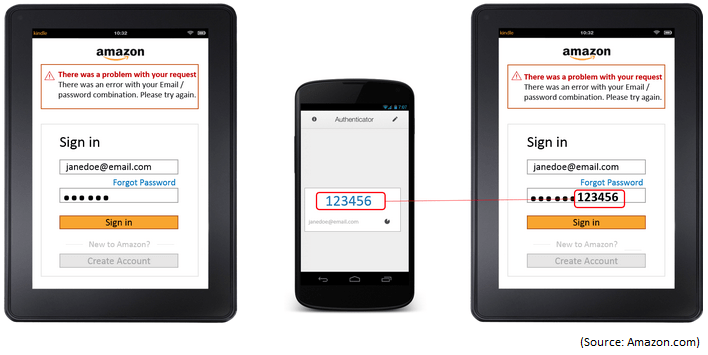
Amazon supports two-step verification for users when they sign into their account. Amazon uses the term verification, instead of authentication. If two-step authentication is enabled, the user enters the username and password, together they are considered a single-factor, as discussed earlier. The user then enters the second verification, which is the code displayed on the Authenticator App, at the end of the password. The code on the app changes every 30 seconds and is synchronized with the code on the server. Even though the type of information is coming from a very different source, one from the user and the other from an app that user has no control over, they are both pieces of information that the user possesses and therefore not two different factors.
Now that we know the clear distinction between the multi-factor authentication and multi-step authentication, what if you use fingerprint and facial recognition? I think you guessed that right. They both use the same factor so it would be considered a single-factor authentication.

As you can see, it’s important to know the difference between the multi-factor and multi-step authentication. It’s also important to realize that both multi-factor and multi-step authentication methods offer a higher level of security and makes it difficult for hackers to breach security.
Additional Reading
Here are some additional articles that you may be interested in reading.
- Microsoft Authenticator to Allow Phone Sign In Without a Password
- Best Practices for Configuring Multi-factor Authentication in Office 365
- How to Setup LastPass for PIN Authentication on Your Smartphone
| Thanks for reading my article. If you are interested in IT training & consulting services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2018 SeattlePro Enterprises, LLC. All rights reserved.