Protecting Your Windows Servers & Clients from the PrintNightmare Vulnerability

The United States Cybersecurity & Infrastructure Security Agency (CISA), CERT Coordination Center (Cert CC), and Microsoft have issued an urgent security warning about a flaw in the Windows Print Spooler service, known as PrintNightmare. By default, the Print Spooler service runs on all Windows servers and clients, so you can only imagine why CISA and Microsoft are freaking out. The flaw allows a standard user to control any Windows computer that’s running the Print Spooler service. The attack can be absolutely devastating.
What is Print Spooler Service?
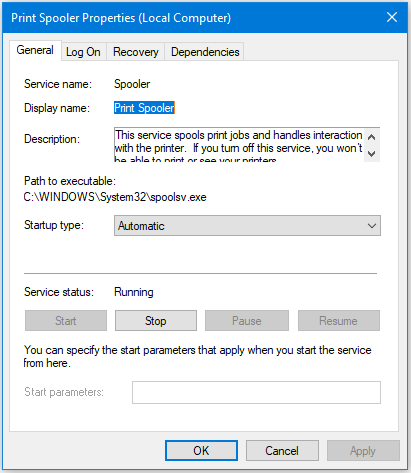
The Print Spooler service is responsible for printing jobs and handles the interaction with the printer on Windows servers and clients. If this service is disabled, you won’t be able to print a document or see your printers. To manage the Print Spooler service on a Windows computer, go to the Services Console (services.msc). On the General tab, you can start, stop, pause, or resume a a paused service. You can also change the service Startup type to Manual, Automatic, Automatic (Delayed Start), or Disable. You will also find several additional options on Log On and Recovery tabs. Usually there is no need to configure additional options, but it’s useful to know what they are, in case you need them.
What is PrintNightmare?
The remote code execution exploit in the Windows Print Spooler service is called PrintNightmare. According to Microsoft, “An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” This is a serious flaw and it applies to all versions of Windows computers. There are many ways an attacker can take advantage of this flaw. For example, an attacker can use phishing to gain access to a Windows 10 computer on your internal network and then use the remote execution code exploit in Windows Print Spooler on a Domain Controller running Active Directory to potentially take over your entire network. Using PrintNightmare for cyberattack is relatively easy because it requires low level of privileges before successfully exploiting the vulnerability and it requires no user interaction.
Didn’t Microsoft Issue a Patch for PrintNightmare in June?
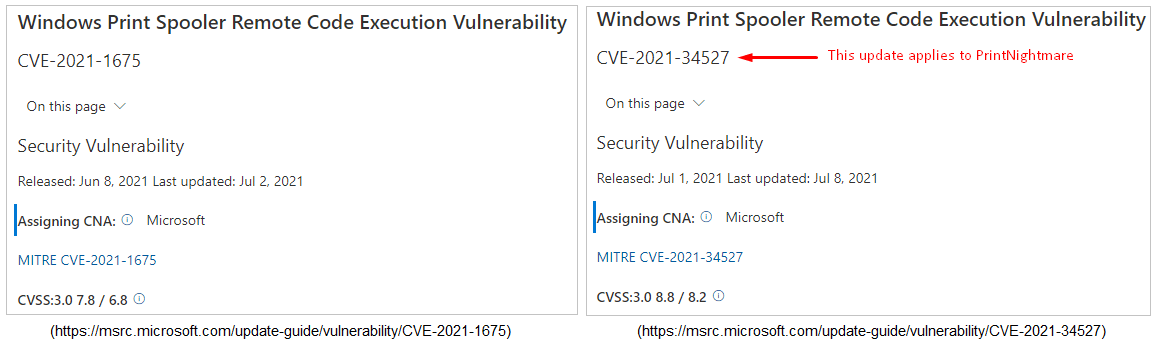
No, on June 8, 2021 Microsoft issued CVE-2021-1675 and updated it on July 2, 2021. For PrintNightmare, Microsoft issued CVE-2021-34527 on July 1, 2021 and updated it on July 8, 2021. It’s easy to get confused because one was released on June 8 and the other was updated on July 8. Having the exact same tittle “Windows Print Spooler Remote Code Execution Vulnerability” also adds to the confusion.
What Should You Do?
Install the July 2021 Cumulative Update on all your Windows computers ASAP. Yes, all Windows computers are vulnerable so make sure you install the update on Windows 10 (and other) clients as well as all your Windows servers.
Verify You Have the Correct Security Update
It’s important to verify that you have the correct Microsoft security update installed on your Windows server or client. These instructions apply to Windows server and Windows 10 clients.
- In the Windows search box type Settings and press Enter.
- In the Settings app, select Update & Security.
- In the Windows Update section select View update history.
- Depending on your computer (Windows Server 2019, Windows 10, etc.) you will see the 2021-07 Cumulative Update installed under Quality Updates section as follows.
Other Workarounds
If for some reason you’re unable to apply July 2021 Cumulative Update on your computer(s), Microsoft recommends the following options as a workaround.
- Disable the Print Spooler service.
- Disable inbound remote printing.
Option #1: Disable Print Spooler Service
If you disable the Print Spooler service on a computer, your computer would be more secure because of the security issues associated with the Print Spooler service. The consequences of this action are as follows:
- You won’t be able to print from your computer to a locally attached printer or to a remote printer.
- If this computer is configured as a print server, no one else will be able to print to the printers you’ve shared on this computer.
- You won’t be able to print to a PDF file.
- You won’t be able to see the printers installed on your computer.
If you chose option #1, you can disable the Print Spooler service either using the graphical user interface (GUI) or the Windows PowerShell.
Use GUI to Disable the Service
- Start the Services Console (services.msc) on your computer.
- In the Startup type dropdown box select Disabled and then Stop the service to prevent other computers from using the Print Spooler service and exploit any vulnerabilities.
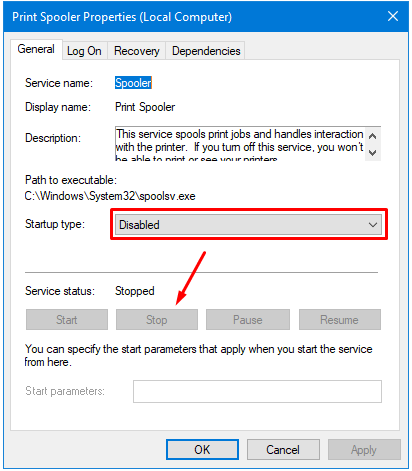
- Click OK to close the box.
| CAUTION! If you disable the Print Spooler service on a Windows computer by changing the Startup type to Disable, make sure you also stop the service. Otherwise, the service will continue to run and may be exploited by an attacker. The Startup type will only come into play when the computer is restarted. |
Use Windows PowerShell to Disable the Service
Windows PowerShell can come handy in a business environment where you want to disable Print Spooler service on a large number of computers. Use the following commands to first stop the service and then disable the Startup type of the service.
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Option #2: Disable Inbound Remote Printing
If you disable the inbound remote printing on a computer, your computer would be more secure because you’re not allowing anyone else to access your computer and use it as a print server. However, you will be able to print to a printer that’s attached to your local computer because your Print Spooler service is still running. This option requires configuring Group Policy. Here’s how.
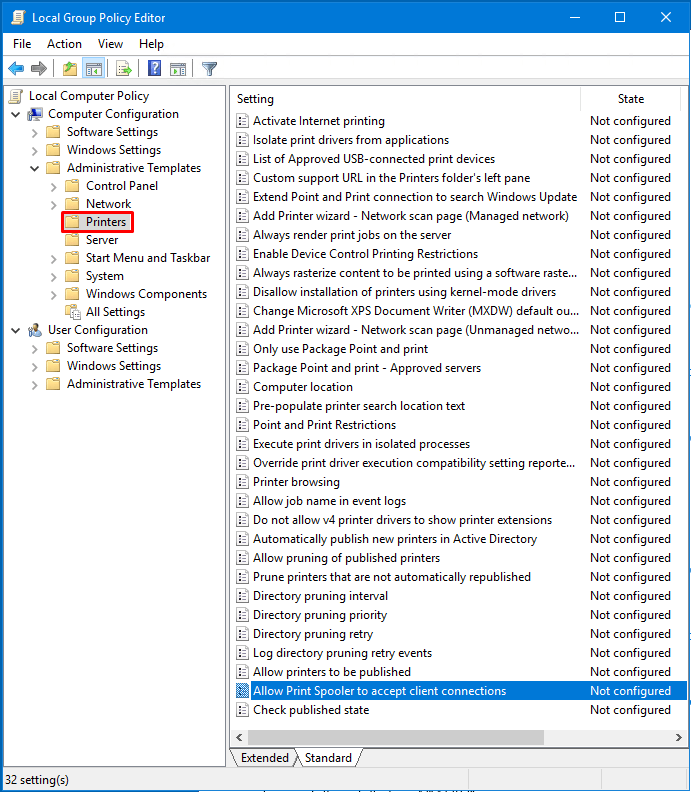
- On your Windows server, use Start -> Run -> gpedit.msc to start the Group Policy Editor console. You can also use the Windows search box to search for gpedit.
- Go to Computer Configuration -> Administrative Templates -> Printers.
- Double-click the entry Allow Print Spooler to accept client connections.
- Select the Disabled radio button and then click OK. This will prevent the print server from accepting inbound remote printing connections from other computers and make your server more secure.
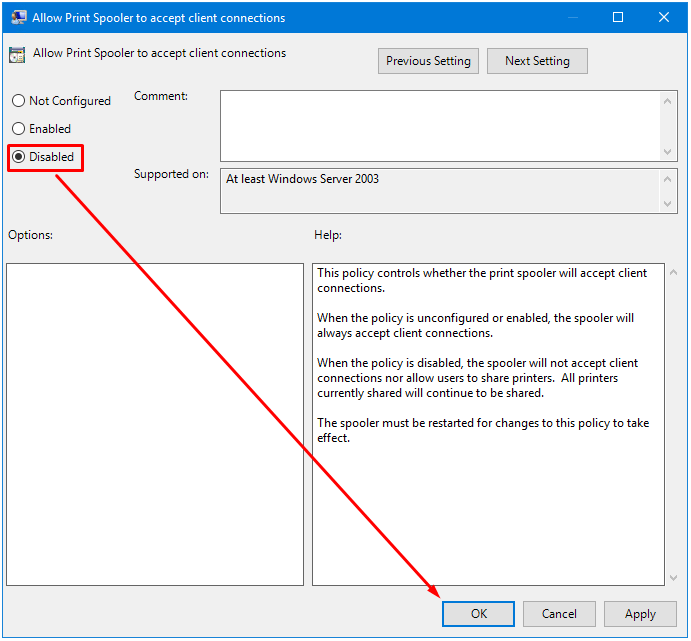
- Restart the Print Spooler service so the Group Policy change can take effect.
| Thanks for reading my article. If you are interested in IT consulting & training services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2021 SeattlePro Enterprises, LLC. All rights reserved.


