Is SMB Relay Attack That Leaks a User’s Credentials to Attackers a Flaw in Active Directory?

On March 21, 2001, Cult of the Dead Cow member Josh Buchbinder, also known as Sir Dystic, released a couple of computer programs called SMB Relay and SMB Relay2 at a convention in Atlanta, Georgia. Sir Dystic is also the author of other hackers tools, such as Back Orifice (a pun on Microsoft’s Back Office), NBName, NetE, etc. The Server Message Block (SMB) relay, or “SMB Relay” for short, and SMB Relay2 are programs that allow an attacker to execute a man-in-the-middle (MITM) attack by intercepting the packets between a Windows client and a server, relaying them back to the server and then authenticating as the user.
Back in 2001 it was believed that the SMB relay attack only worked in a local area network (LAN). By the way, Microsoft patched that security hole about 7 years later in 2008. Fast forward to 2015. Researchers have revealed that the SMB relay attack works not just on a LAN, but also over the Internet, as reported by Information Week on August 5, 2015 in the article New SMB Relay Attack Steals User Credentials Over Internet. A couple of days later there was another article on the PCWorld.com Web site titled Researchers find way to steal Windows Active Directory credentials from the Internet. That sounded like a pretty major flaw in Active Directory that’s allowing people to steal Active Directory credentials over the Internet. But is it really a flaw in Active Directory? Let’s take a closer look at what’s going on here.
First I am going to explain what an SMB protocol is and then I will explain how the SMB Relay attack works. Once you have a good understanding of the two then I will give you my 2 cents about this attack, discuss whether this is a flaw in Active Directory, talk about the potential risks to a business, and offer some options for dealing with this attack.
What’s SMB?
In case you are not familiar with SMB, it’s a file sharing networking protocol that can be used on top of TCP/IP or other network protocols. In Windows environment, it’s implemented as Microsoft SMB protocol. In simpler terms, Microsoft SMB is a client-server protocol that allows the users or applications to communicate with the server. Windows Server 2012 R2 and Windows 8.1 introduced SMB version 3.02 which, among other things, can be used by SQL Server to store database files on SMB file shares and by Hyper-V to store virtual hard disks (VHDs) and snapshots in file shares. Here’s an overview of the process that takes place.
- The client and server establish a NetBIOS session.
- The client and server negotiate the Microsoft SMB Protocol dialect (i.e. version).
- The client logs on to the server.
- The client connects to a share on the server.
- The client opens a file on the share.
- The client reads from the file.
How SMB Relay Attack Works
There’s a lot of information on the Web about SMB Relay and how it works but I think Mark Baggett’s article written for SANS in April 2013 was an interesting one and explains nicely how the SMB Relay attack works. The article is called SMB Relay Demystified and NTLMv2 Pwnage with Python.
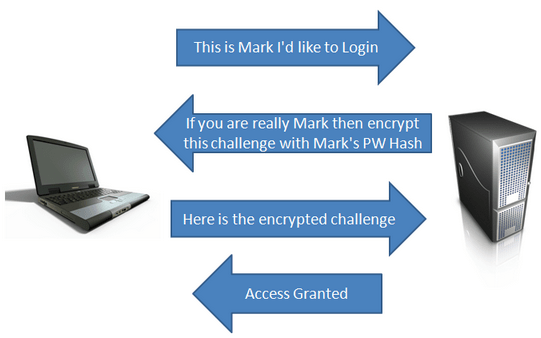
SMB supports NTLM encryption, which is a challenge/response protocol. When the user tries to get authenticated by the server to establish a session, this is what happens in layman’s terms.
- Client: I want to to login.
- Server: Okay, then prove me your identity by using your hash to encrypt my challenge.
- Client: Here’s my encrypted challenge.
- Server: You are allowed access. (The server only allows access if it was able to successfully decrypt the encrypted challenge with the user’s password hash, otherwise access is denied.)
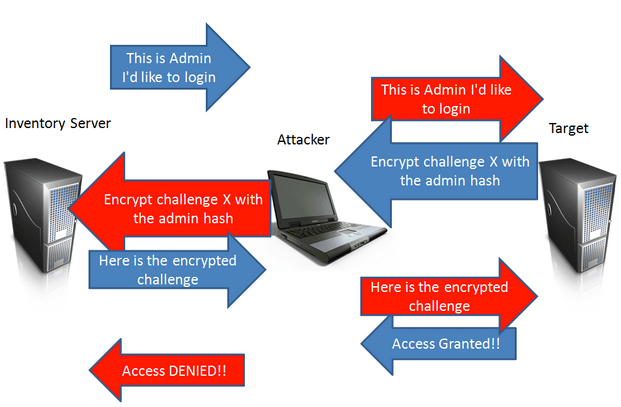
Now let’s look at the scenario when the SMB Relay attack is used. Mark Baggett describes exactly how the SMB Relay attack takes place:
“With SMB Relay attacks, the attacker inserts himself into the middle of that exchange. The attacker selects the target server he wants to authenticate to and then the attacker waits for someone on the network to authenticate to his machine. This is where rogue host detection, vulnerability scanners, and administrator scripts that automatically authenticate to hosts become a penetration tester’s best friends. When the automated process connects to the attacker, he passes the authentication attempt off to his target (another system on the network, perhaps a server). The target generates a challenge and sends it back to the attacker. The attacker sends the challenge back to the originating scanning system. The scanning system encrypts the hash with the correct password hash and sends it to the attacker. The attacker passes the correctly encrypted response back to his target and successfully authenticates. This process is shown in the next illustration. The BLUE arrows are the original communications and the RED arrows are slightly modified versions of those communications that the attacker is relaying to his target, so that he can gain access to it.”
This is only a small snippet from Mark’s article. There’s a lot more in his article that you might be interested in.
Stealing User Credentials Over the Internet
The reason SMB Relay attack is back in the news is that originally it was believed that the SMB Relay attack only worked on a LAN. Recently two engineers from Salesforce.com demonstrated that SMB Relay attack can be used from the Internet to attack a network and take over a server. The attacker can just wait for someone to access a rogue Web site, or trick a user into visiting his Web site and loading an image in IE, capture the SMB login credentials (plaintext username and user’s password hash) and then crack the password hash. Keep in mind, by default Internet Explorer allows automatic login in the intranet zone because intranets are on internal, private networks and are considered secure. Therefore, information such as your domain and NetBIOS name of the computer is sent in unencrypted plain text. With SMB Relay attack, the attacker can intercept the communication (challenge/response exchange) between the client and the server as I explained earlier and send the user’s credentials to the target server to gain access.
If you are interested in all the gory details about SMB and file sharing then check out this white paper from Blackhat.com “SMB: Sharing more than your files….”
The Link Between Active Directory and SMB Relay Attack
The aforementioned PCWorld article gives the impression, at least based on its headline, that the SMB Relay attack is due to a flaw in Active Directory. That in my opinion would be really a stretch. The SMB Relay attack over the Internet has to do with the Web browser, and the user being tricked in visiting a rogue Web site and loading an image, and Internet Explorer’s default setting that is configured to trust intranet zone. None of this have anything to do with Active Directory in the sense that even if you were using a different Directory Service, e.g. Novell Directory Services (NDS), you will still have the same issue. Now you could argue that the weaknesses in the browser or SMB protocol is to be blamed. You can blame the NTLMv2 protocol that is used for authentication. You can even blame uneducated users for getting tricked in the first place to visit an unsafe Web site. Perhaps some might even blame the operating system or the computers that are attached to an Active Directory domain, but I don’t believe that there is anything flawed in Active Directory that can be attributed to or somehow linked to the SMB Relay attack.
Perhaps the author didn’t mean to give the impression that Microsoft’s Directory Services is to blame for the SMB Relay attack but because a lot of feeds on the Web have been relaying PCWorld’s headline “Researchers find way to steal Windows Active Directory credentials from the Internet“, I wanted to make it clear that in my opinion, the researchers so far haven’t revealed a bug or a flaw in Active Directory that can be directly linked to SMB Relay attack. The researchers have definitely revealed something new that we should be aware and concerned about and Microsoft should be taking appropriate actions to secure the operating system and networking protocols (like SMB and NTLM, or come up with alternatives), but that’s a different topic. The PCWorld’s sensational headline is misleading.
Are You at Risk?
On paper this all makes sense but there are a few assumptions made in this scenario. In other words, every single person and network is obviously not at risk. By default, packet signing is enabled, but it has to be disabled for this to work. You have to allow outbound SMB traffic. Your passwords must be weak and you must not have any firewalls or Intrusion Detection System (IDS) on your network. The SMB ports 137, 138, 139, and 445 must also be open. I am not down-playing the risks associated with SMB Relay attack by any means and this shouldn’t put you at ease because you must always be vigilant. The obvious question is, could your business be at risk? The answer is, “it depends.”
I don’t want you to think that you may not be at risk just because your business has a firewall and your passwords are fairly secure. There are lots of factors that play a part in the level of risk to an organization. Just because you have a firewall doesn’t mean that the SMB ports that can create a big hole in your firewall are actually closed. There are different versions of SMB. The new version that is used in newer operating systems, like Windows 10, supports SMB 3.1.1. They all have different levels of security. If you try and disable either SMB or NTLM to secure your network, you may not be able to run the necessary services on your network. In an ideal world, you would disable all the risky protocols and ports, properly configure your firewall(s), educate the users, enforce strong passwords, ensure all your network servers and workstations have the latest updates, etc. but we don’t live in a perfect world. That doesn’t mean that we should give up. Your security team should still spend time to keep up with all the potential dangers and attacks on your network in this ever-changing technological world. Consider these statistics. In 2014, 47% of Americans were hacked and according to USA Today, 43% of businesses experienced data breach. And I haven’t even mentioned all the major hacks in 2015. These statistics alone tell me that we better take security seriously and we must always be vigilant.
What Are Your Options?
If you already have a security team and feel that you have the necessary expertise within your organization then frankly you don’t need my advice. However, if you don’t, then read on. One thing that I recommend is that if you don’t have the in-house expertise, which is usually the case in a small and medium-size (SMB) business, then consider hiring a security company to do an assessment of your network.
The Information Technology (IT) department of smaller organizations are often in a fire-fighting mode putting out network “fires” as fast as they can. They don’t have the expertise and even if they had the expertise they just don’t have the bandwidth to be spending time on security and risk assessments, or the research that is necessary to keep with up the new attacks. A security company can perform a risk assessment of your entire network, including Active Directory, Exchange, SharePoint, SQL Server, routers, firewalls, etc. Depending on the company you hire, they can also analyze your business process, business services and the like, and provide the guidance that your business needs. Based on their assessment report, they can secure your network and minimize the security risks. Based on my experience, when organizations try to implement certain security measures themselves, they run into major challenges due to internal politics and lack of user acceptance. An outside organization can get much better results in this regard and can often overcome these challenges. Try enforcing a 15-character password in your organization and see what happens. I can assure you that you will encounter serious push back. However, if you hire professionals who are used to dealing with these situations you may be pleasantly surprised at the results because good security consultants don’t just know the technology, they also know how to mitigate issues such as internal politics and user-education.
Copyright © 2015 SeattlePro Enterprises, LLC. All rights reserved.