UW Researcher Believes the Next Hacking Frontier is Likely to Be Our Brain

By now, everybody and their brother-in-law knows about the Russian hacking during the 2016 U.S. elections. To say it’s impact has been enormous would be an understatement. When we talk about hacking, we usually mean hacking into electronic devices and digital software. The hackers have successfully hacked into smartphones, computers, refrigerators, and just about anything that’s been connected to the Internet. However, that might change in the future. The University of Washington (UW) researcher Tamara Bonaci believes that hacking the brain is going to be the next frontier.

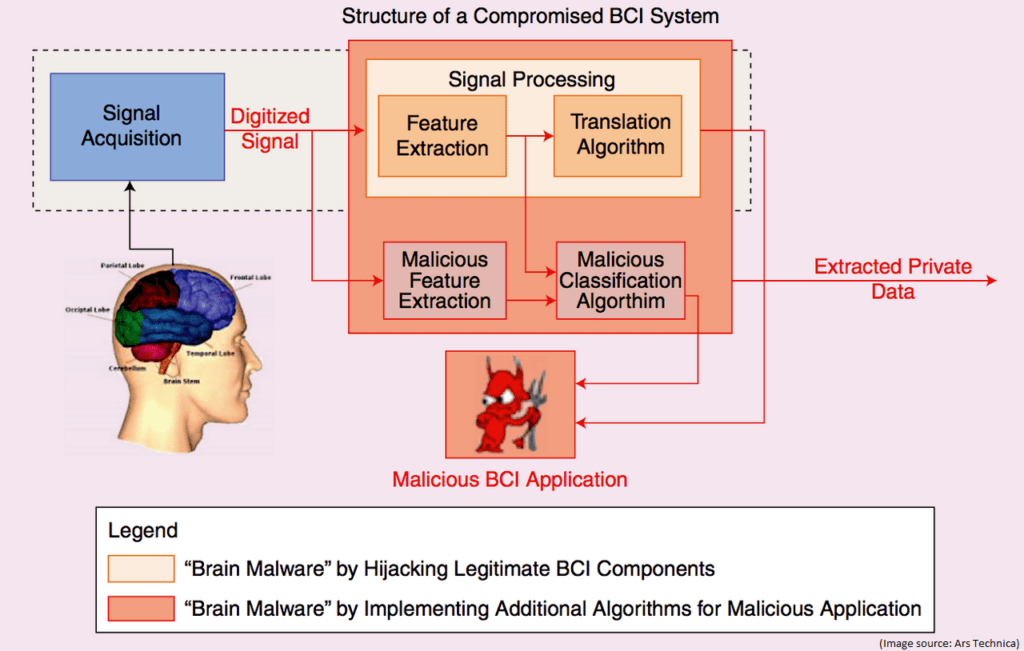
People often say that the human brain is like a computer. That’s true, especially when it comes to computing information. However, our brain is not digital and is not connected to the Internet like an electronic device. So how do you hack into a brain? According to Bonaci, by extracting sensitive information from electrical signals in the brain. In her presentation at the Enigma security conference, Bonaci used a video game to make her point. The video game had seven electrodes connected to a player’s head and measured certain signals in real time. These electrodes formed, what Bonaci called, a brain-connected interface (BCI). According to this article in Ars Technica, the UW research team was able to use the signals measured by BCI to get clues as to what the players were thinking and feeling.
The UW researcher even suggested that electrical signals in our brain should be declared as personally identifiable information (PII). That’s a fascinating idea. According to the article:
“Bonaci said that electrical signals produced by the brain are so sensitive that they should be classified as personally identifiable information and subject to the same protections as names, addresses, ages, and other types of PII. She also suggested that researchers and game developers who want to measure the responses for legitimate reasons should develop measures to limit what’s collected instead of harvesting raw data. She said researchers and developers should be aware of the potential for “spillage” of potentially sensitive data inside responses that might appear to contain only mundane or innocuous information.”
If you are interested in security-related topics, you should check out Ars Technica’s Security Editor Dan Goodin’s complete article for the rest of this amazing story.
Copyright © 2017 SeattlePro Enterprises, LLC. All rights reserved.