Understanding the Impact of Enabling Guest Access in Microsoft Teams

Configuring Guest access in Microsoft Teams is an important part of an organizations strategy. Microsoft announced on December 6, 2020 that it will make some changes to the default settings for Guests in Microsoft Teams, which is part of Microsoft 365. On February 8, 2021, Microsoft turned on Guest access in Microsoft Teams by default for customers who did not configure this setting before the change was made. The new default settings makes it easier for the users of new Microsoft 365 tenants to start communicating with external users, but at what cost? Organizations haven’t spent much time to figure out what exactly the consequences are for this action.
Who is Impacted?
Any organization, new or old, that is concerned about cybersecurity should consider the effect of allowing Guest access to external users. If you must allow Guest access, make sure you understand the various sharing controls and security options to protect your company data and prevent accidental exposure to your confidential data.
If you don’t use Microsoft Teams, or you use Microsoft Teams but have already disabled the Guest access in Microsoft Teams, you don’t need to do anything because you’ve already configured the Guest access setting and secured your Microsoft Teams environment. You are not impacted by Microsoft’s decision.
If you use Microsoft Teams and didn’t even know about this announcement, you should look at your Guest access settings today. Unless you properly configure and secure your Microsoft 365 tenant, including Microsoft Teams, you can potentially be opening up Microsoft Teams and other resources to users that are not part of your organization. This can pose some serious privacy and security risks to your organization. That’s why it’s important to act today.
What Should You Do Now?
Whether you knew about this change or not, I recommend at minimum you look at your Org-Wide settings in Microsoft Teams admin center and configure the following areas within Microsoft Teams admin center.
- External access
- Guest access
- Teams policies
- Meeting policies
- Meeting Settings
This is a good start but if you are concerned about securing your organization, I have a more comprehensive list at the end of this article on how to secure your tenant when you collaborate with external users outside your organization.
Configuring the Guest Settings
Microsoft 365 services and applications are regularly updated to offer enhanced user experience, improved services, and better security to the subscribers. Therefore, your options in your tenant may be somewhat different and your screenshots may not exactly match with what you see in this article.
To configure the guest settings, sign in as a Global Admin to Microsoft 365.
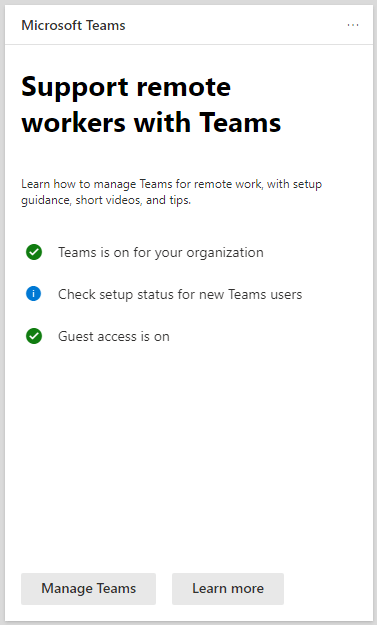
Go to the Microsoft 365 Admin center. You may see the following card that’s designed to support remote workers with Teams. You will find this card handy because there are several settings you can configure by using the links provided in this card.
This card allows you to quickly get to various locations in your Teams. You can click on one of the three links on this page to configure your Teams, or select one of the two links at the bottom of the card. For example, you can check the setup status for new Teams users and for security reasons turn the guest access off. Notice by default, it’s on. Selecting Learn more will take you to a Microsoft article no how to Support remote workers using Microsoft Teams. The Manage Teams link offers you the following configuration options. This is a good place to easily manage your Teams licenses and configure guest access. You also have a link to Go to the Teams admin center.
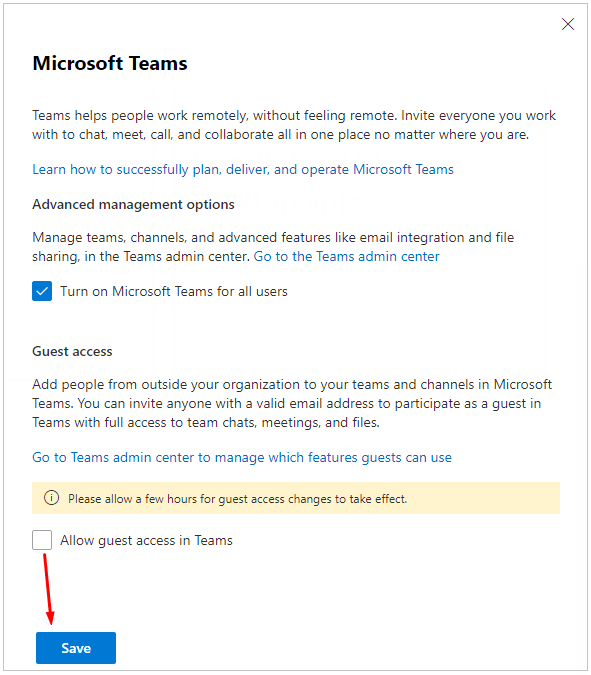
Turning Off Guest Access
By default, your organization can communicate with all external users and all guest users. To turn off the guest access, click the link Manage Teams in the above screenshot. You will see the following screen pop up in the right part of your monitor to configure various Teams options. Because the guess access is enabled by default, the Allow guest access in Teams box is checked. Clear the box to turn off guest access.
Visit Microsoft for more information on this topic.
Is Enabling Guest Access Always Risky?
No. You can enable the Guest access and still properly secure your Microsoft 365 tenant, as long as you plan for Guest access and understand the risks. For example, you can enable the Guest access and then turn on or off certain features that guests may or may not be able to use. This would limit their access and offer some degree of protection in Microsoft Teams. However, that’s not all there is to prevent risk to your business assets. Guest access should be one part of your overall strategy for allowing access to external users. There’s a laundry list of things that you need to do to properly secure your Microsoft 365 environment from all external users. I list some of them in the next section.
| Risks Posed by External Users: The risks posed by external users are not because they are not trustworthy, the risks have more to do with the fact that they are not part of your organization and therefore are not bound by your organization’s policies and procedures, they may not have signed proper Non-Disclosure Agreement (NDA), their network and their devices may not be as secure as yours, and they often use free web-based emails (Gmail, Yahoo, Outlook.com, etc.) to access your network which poses a higher risk. Don’t forget, when we connect to other organizations, we are the external users for them and we pose these dangers to them. I should also point out that not all external users pose a security threat and the risk of accidental exposure to confidential data concerns many administrators. |
Remember, we are not talking about creating an isolated extranet for the external users and giving them controlled access to their extranet portal. We are talking about letting guest users into our “internal private network” where they may be able to see, hear, record, publish, delete, share, and modify data on our network as they work in teams and channels on our network. The risk of accidental exposure is very high.
What To Do If You’re Concerned About Security
If your organization is concerned about cybersecurity attacks and has a need to communicate with the external users (who doesn’t?), there are a bunch of things you have to do to protect your organization. Although every organization is different, in general it’s a good idea to configure at least the following to safely communicate with external users.
- External collaboration settings in Azure AD
- Teams external access settings
- Teams guest access settings
- Microsoft 365 Groups guest settings
- SharePoint organizational level sharing settings
- SharePoint organizational-level default link settings
- SharePoint site-level sharing settings
- Azure conditional access policies for guests
- Guest access reviews
- Data Loss Prevention (DLP) policy to prevent unwanted guest sharing of sensitive content
- Session timeout policy to ensure guests authenticate daily
- To reduce the attack surface, limit guests to web-only access for unmanaged devices
This is not a complete list by any means. Depending on the level of security that’s necessary, there’s more that needs to be done to plan for Guest access to your network and placing proper security controls to protect your organization. Simply put, there’s a lot of planning that needs to take place before you start communicating with the external users in Microsoft 365.
| Thanks for reading my article. If you are interested in IT consulting & training services, please reach out to me. Visit ZubairAlexander.com for information on my professional background. |
Copyright © 2021 SeattlePro Enterprises, LLC. All rights reserved.